Introduction:
This article looks at Active Directory Flexible Single Master Operation roles. Its important to know what these roles do within your Active Directory environment and how to identify what Domain Controller holds these roles. It's more important to know when you are replacing Domain controllers and demoting out older domain controllers as you can potentially break certain functions of your domain.
I will cover each role individually at a high level and how to identify the role holders in both server GUI and PowerShell. How to transfer these roles between Domain Controllers with numerous tools. We will also look at a disaster recovery scenario where the role holders have been removed from the domain and we must "Seize" them back
What are Flexible Single Master Operations Roles?
Active Directory works in a multi-master model, meaning I Can make changes on any DC in my forest and it will replicate. While this is great it potentially opens up room for replication errors or conflicts. FSMO roles provide a way to prevent conflicts, where certain changes are made by certain Domain controllers that hold a FSMO role.
There are 5 roles in total, 2 work forest-wide level and 3 work at the domain level:
Forest Level FSMO Roles
Schema Master
Domain Naming Master
Domain Level FSMO Roles
RID Master
PDC Emulator
Infrastructure Master
Roles functionality
Schema Master
Responsible for updating the directory schema. Once a change has been made or the schema has been extended it will then replicate the changes made to other domain controllers.
Domain Naming Master
Responsible for making changes to the forest-wide domain name space and can add and remove a domain from the directory.
RID Master
Each security Principal in AD (User/Group etc) has a SID and a unique RID applied, The owner of this role controls the allocation of RID pools to fellow domain Controllers to use when creating objects. IF RID pools run out on a Domain Controller it will check in with the RID FSMO holder to extend it's RID pool.
SID = matches the domain the security principal is created in. RID = Unique value for each security principal created.
PDC Emulator
Responsible for the synchronization of time between Domain Controllers. Make a password change in AD and the change is notified to the PDC. PDC also controls account lockouts when you fail your password entry numerous times. Authentication failures are also notified to the PDC.
Infrastructure Master
Responsible for updating an objects SID and distinguished name in cross-domain object reference. This role is pretty much superseded if each Domain Controller is a Global Catalog.
Identifying FSMO Role Holders
Server GUI:
Active directory Schema Snap-in - Schema Master
This must be enabled via CMD with the following command:
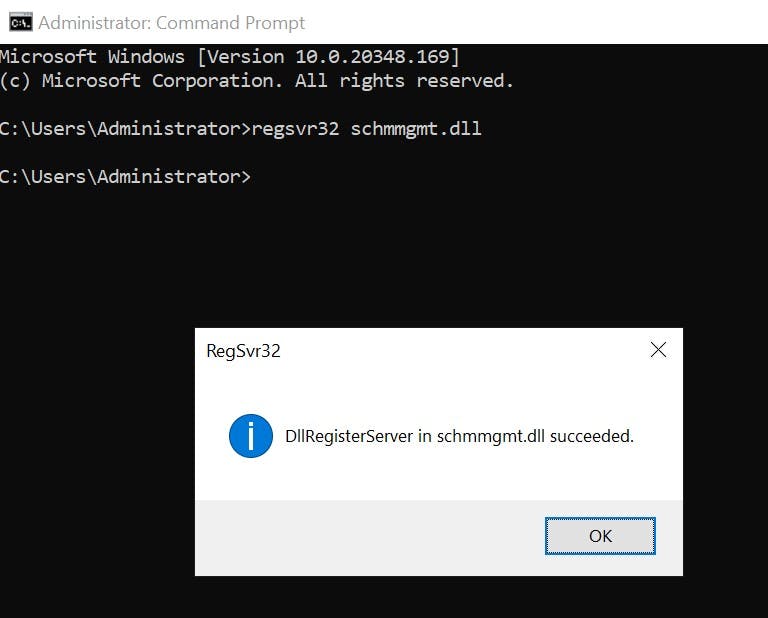
You will get a popup saying it has been enabled. You can then load mmc.exe and you will see "Active directory Schema" Snap-in. Right-click on top level and select "Operations Master"
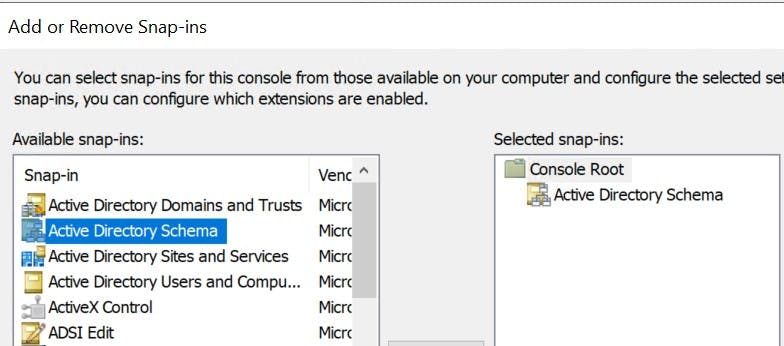
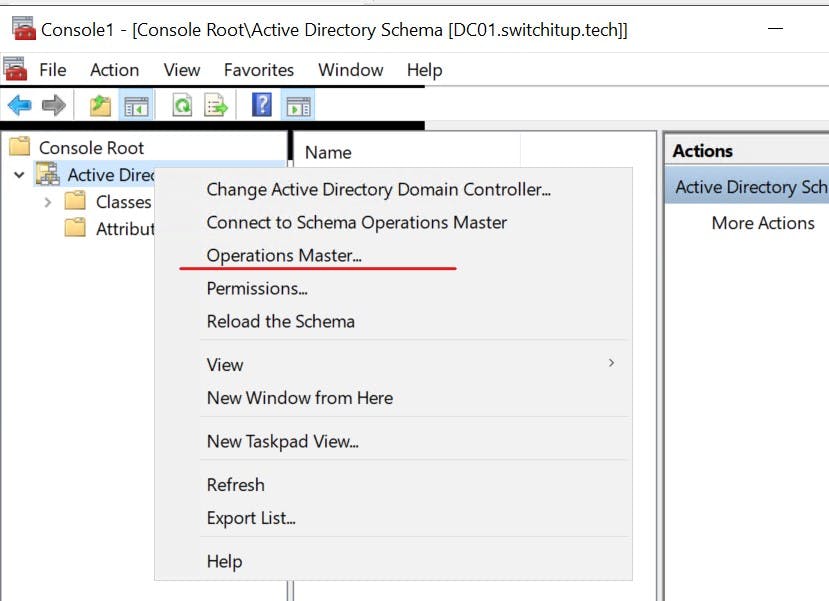
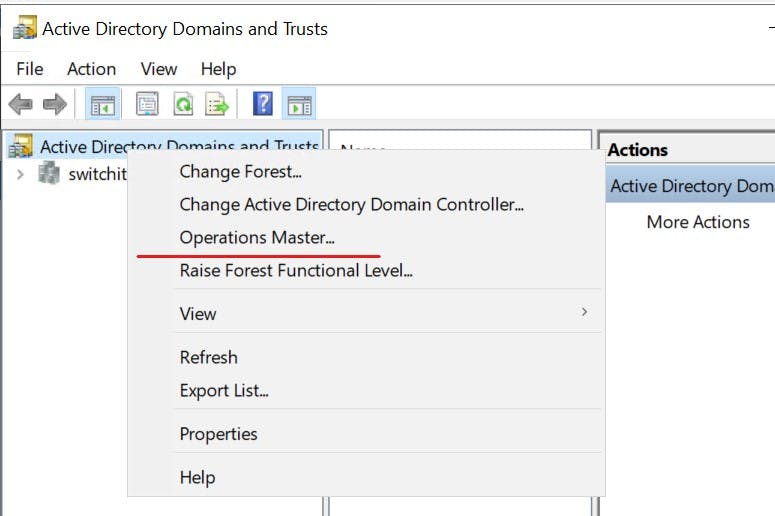
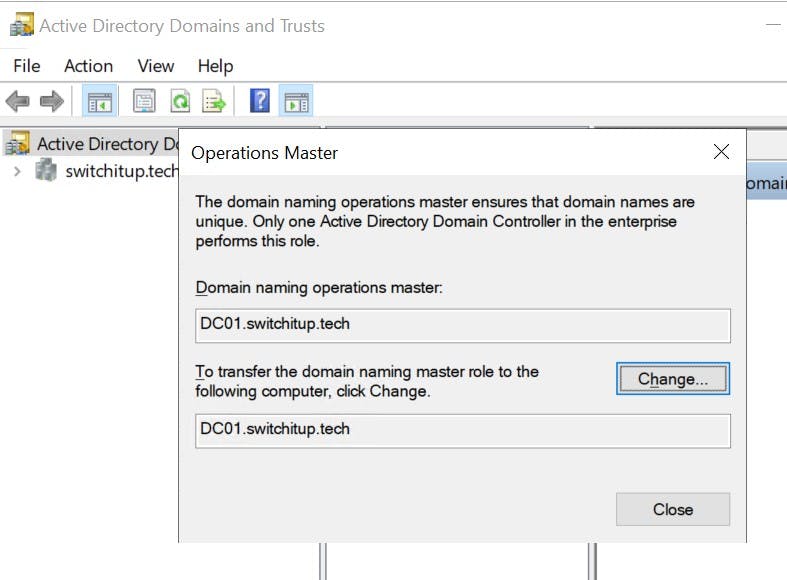
Active Directory Domains and Trust - Domain Naming Role
Right-click top level and select "Operations Master"
Active Directory Users and Computers - RID/PDC/Infrastructure Roles
Right-click the domain and select "Operations Master"
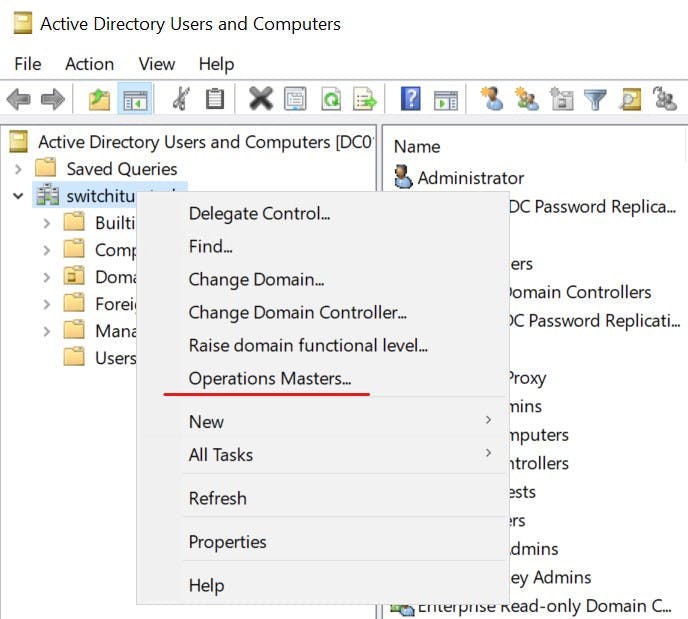
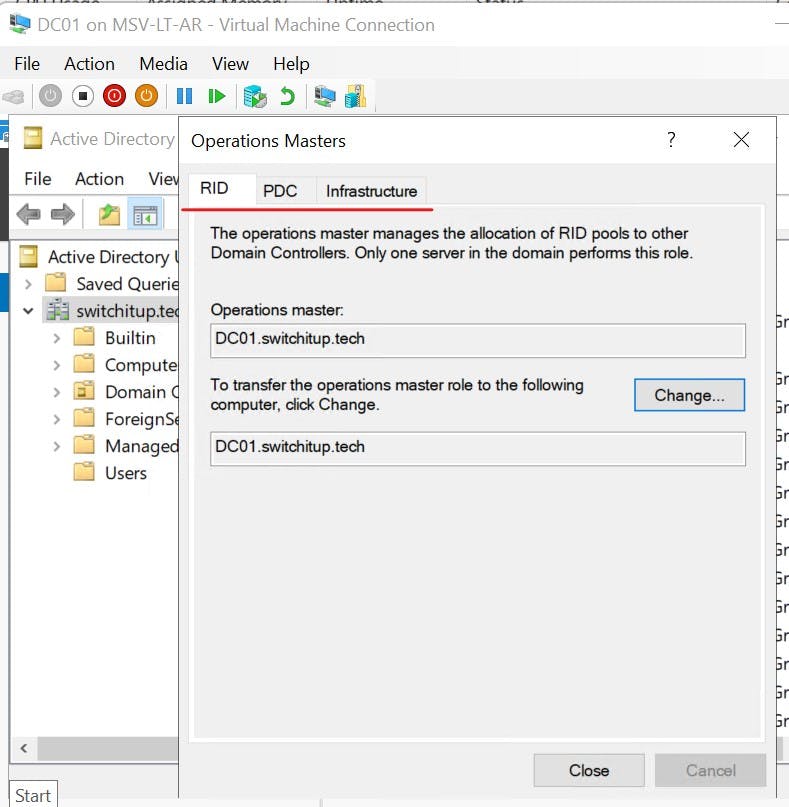
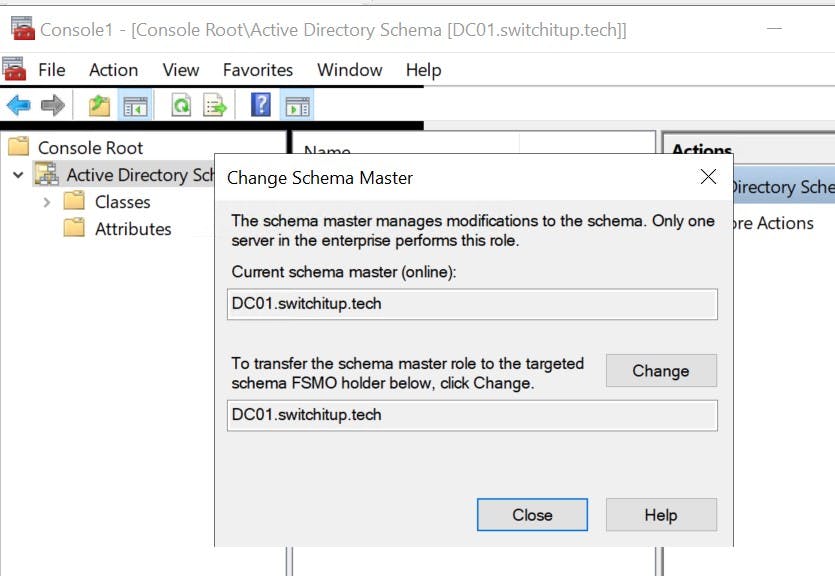
Notice on each of these you can change the role holder. If you have more then one Domain Controller in your environment you can navigate to the Operations Master tab on the Domain controller you want to transfer ownership to and select "Change" If you plan to remove/demote a domain controller that holds a role it is strongly recommended you change the role holder this could be to an existing DC that you plan to keep or a new DC you have promoted in. More on this shortly.
PowerShell
Get-ADForest
Domain naming and Schema Master
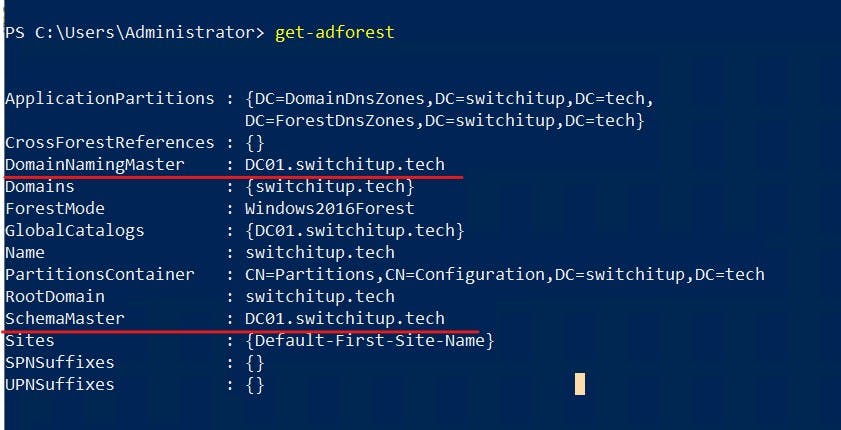
Get-ADDomain
RID/PDC/Infrastructure Masters
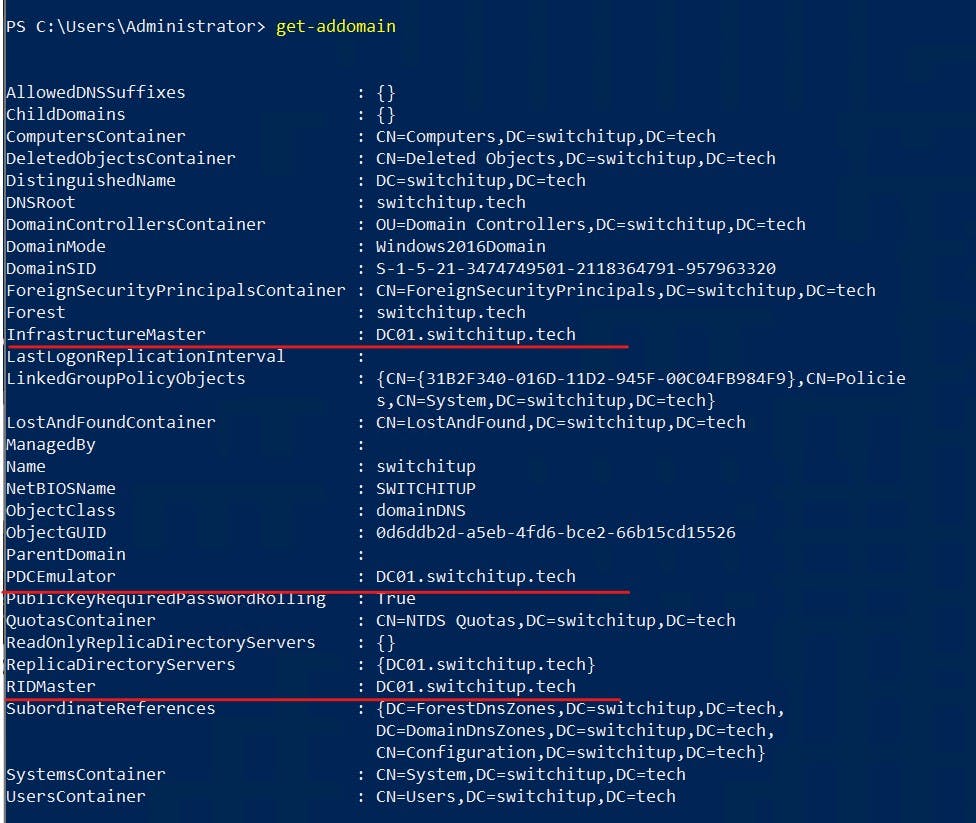
NETDOM
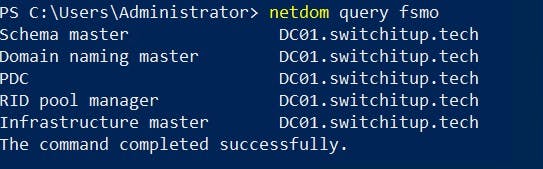
netdom query fsmo
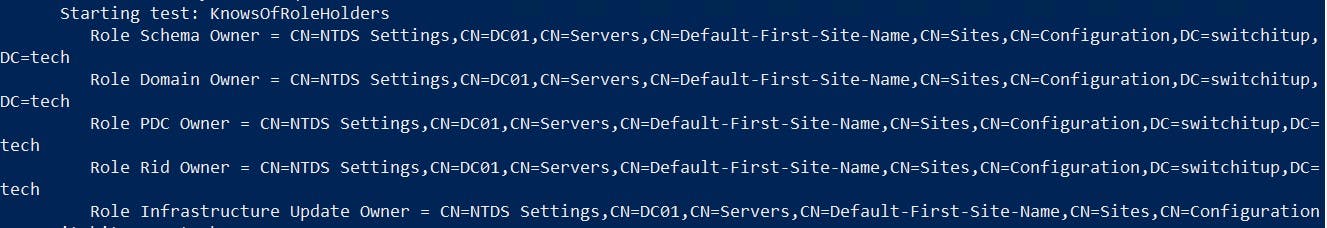
Dcdiag
DCdiag /test:Knowsofroleholders /v
Halfway down the output you will see the owner check, this example, DC01 owns all Roles as this is my only Domain Controller
Transfer/Seize Roles
In recommended best practice you transfer the roles to a Domain Controller you are going to keep in the domain, we saw this briefly above with the "Change" button.
But what if the Apprentice has built and promoted new Domain Controllers on the latest OS then demoted out your role holders and forgot to move the FSMO roles?
Then you are going to have to Seize the roles as a final resort and this should only be if the original holder(s) are non contactable, I.e never going to connect back to the domain again because they don;t exist anymore.
PowerShell - Transfer
Example 1 - Move PDC Role to USER01-DC1
Move-ADDirectoryServerOperationMasterRole -Identity "USER01-DC1" -OperationMasterRole PDCEmulator
Example 2 - Move PDC and SCHEMA Master to USER01-DC1
Move-ADDirectoryServerOperationMasterRole -Identity "USER02-DC2" -OperationMasterRole PDCEmulator,SchemaMaster
Example 3 - Move All roles to Specific Domain Controller
$Server = Get-ADDomainController -Identity "TK5-CORP-DC-10.fabrikam.com" Move-ADDirectoryServerOperationMasterRole -Identity $Server -OperationMasterRoleSchemaMaster,DomainNamingMaster,PDCEmulator,RIDMaster,InfrastructureMaster
PowerShell - Seize
Move-ADDirectoryServerOperationMasterRole -Identity USER04-DC1 -OperationMasterRole RIDMaster,InfrastructureMaster,DomainNamingMaster -Force
Notice "-Force"
NTDSUTIL.EXE
NTDSUTIL.EXE is a command line program you can use to manage domain partitions, snapshots, recovery of objects and FSMO Role Holders. (to name a few)
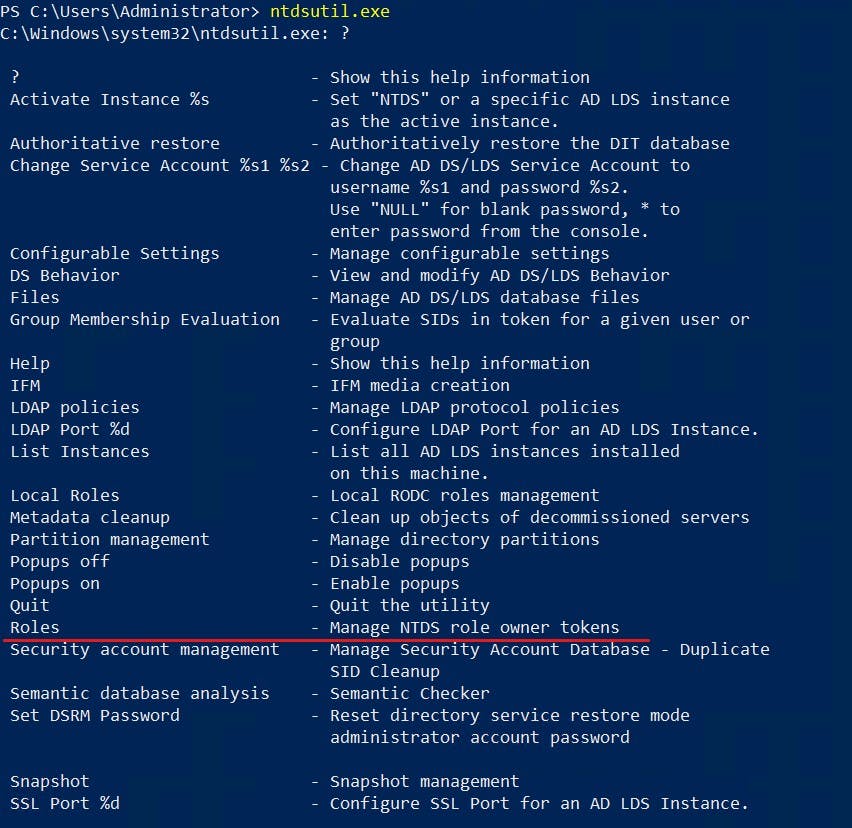
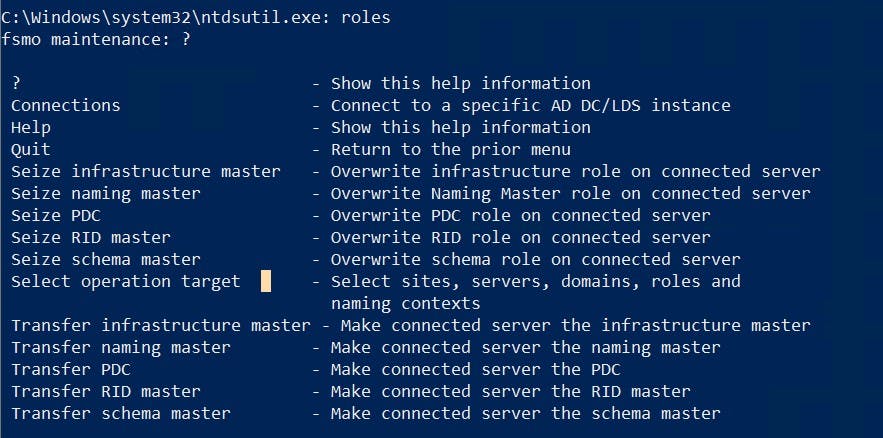
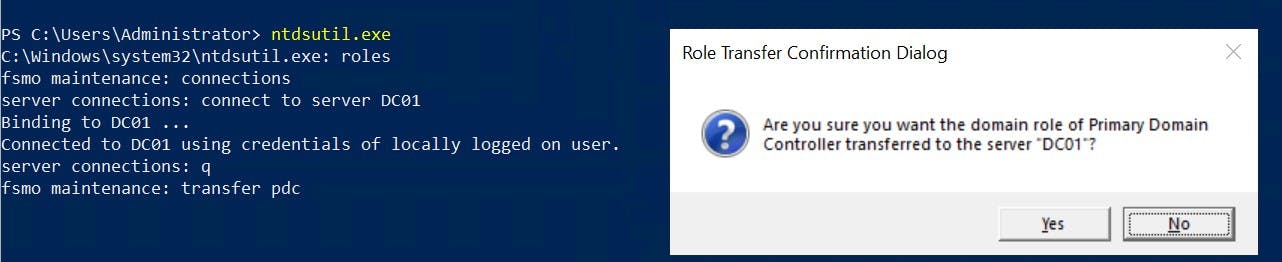
Example Transfer with NTDSUTIL
Summary
You have learned what FSMO role holders are and their responsibilities, how to safely transfer these as best practice or in a worse case disaster scenario, seize the roles back via a number of different tools and methods.
Hope you found this informative, thank you for reading, please give a like or a comment to support.
