Background
In the first article we built an Azure Virtual Desktop lab that consisted of cloud only infrastructure. We deployed Storage accounts ready for FSLogix profile containers and we created an instance of Azure Active Directory Services (AADDS) so we can use domain join/NTFS and other benefits we would get if we had synced an on premise domain via AD Connect.
We then deployed a host pool with a session host via the "create a host pool" wizard
If you missed that article or need a reference of what's been deployed or refresher you can check the link out below!
switchitup.tech/setting-up-an-azure-virtual..
Second article looked at how we connect our users to our AVD infrastructure using remote desktop client and web client. Check that out at the following link:
switchitup.tech/how-to-connect-to-azure-vir..
Introduction
We will build on from our base lab setup and cover how to lock down access to your AVD sessions using conditional access that will force MFA on login to the Remote Desktop Client.
Pre-requisites If you have followed on from the lab build hopefully you are using a 365 developer account which gives you access to 365/Azure tenant with full E5 licensing and P2 Azure Active Directory.
- Conditional Access requires P1 Azure Active Directory licensed Tenant
Verify by navigating to:
Azure Portal > Azure Active Directory
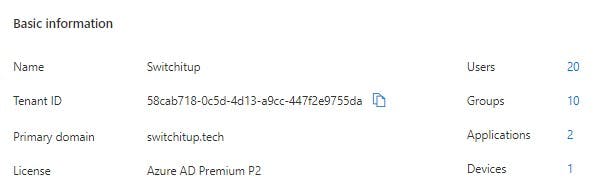
- Global Admin Access
What is Conditional Access?
Conditional Access can be used as a way to allow or deny users access to cloud resources based on a number of conditions. A number of examples include:
- Device Must be hybrid AD joined
- Device must be Intune Compliant
- Must be connecting from a trusted location -Requires Multi-Factor Authentication
While not probably as important for Corporate devices that sit on an internal network but especially important for environments that adopt Bring your own Device (BYOD). You can verify device conditions before users get access to corporate resources.
How to Find Conditional Access in Azure
Navigate to:
Azure Active Directory > Security > Conditional Access
Here you will find any existing policies that may be applied. Or none in our case.
Creating a conditional Access Policy
Click on "New Policy"
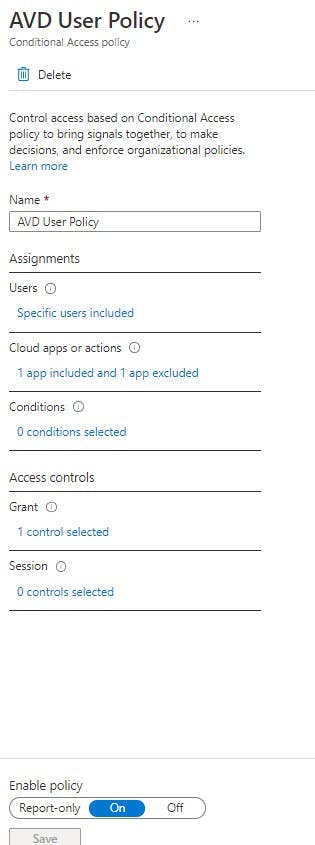
We will name this "AVD User Policy" but feel free to change. I will walk through each section as we go:
Assignments: Users
Here we can select the user or group this policy will apply to OR even exclude. For now we want to INCLUDE AVD_USERS as members of this group have access to AVD.
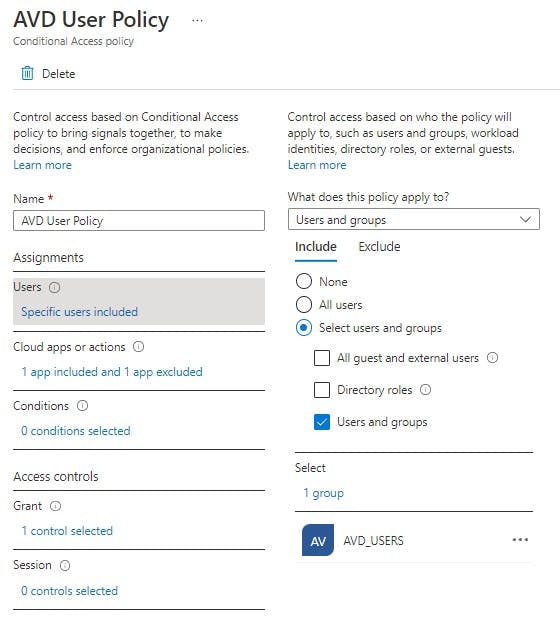
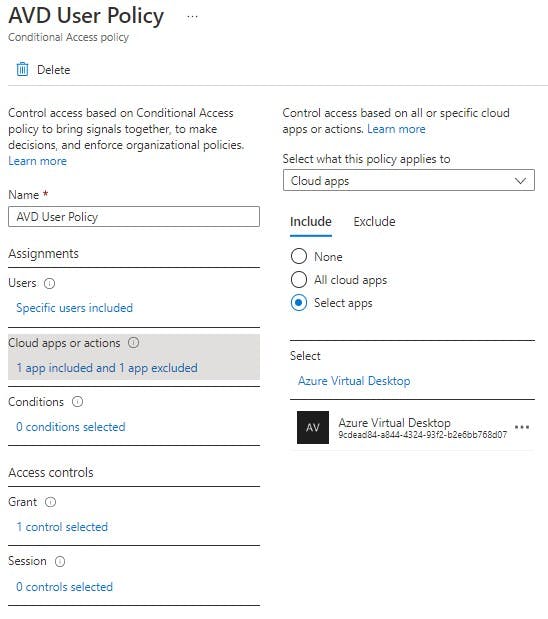
Assignments: Cloud Apps or Actions
The great thing about Conditional Access is you can assign it against any applications you bring into your Azure AD Tenant. You can lock down 365 Apps/ 3rd party apps. Here we are going to select "Azure Virtual Desktop".
Assignments: Conditions
Control access based on signals from conditions like risk, device platform, location, client apps, or device state. You can set things like network IP's if all staff work in UK you wouldn't expect to see logins from China. You can even check for the OS the user is using. We will leave this blank.
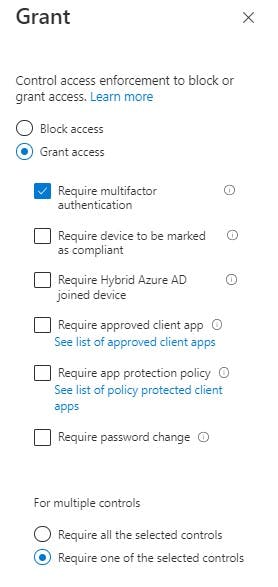
Access Controls: Grant
If the above matches GRANT access but enforce X control. Here we can say grant access to AVD if the user is in AVD_USERS BUT force MFA authentication. Only apply this single control. You can force it to apply additional Grant controls that the user must complete to be allowed access (see tick boxes at bottom of the blade)
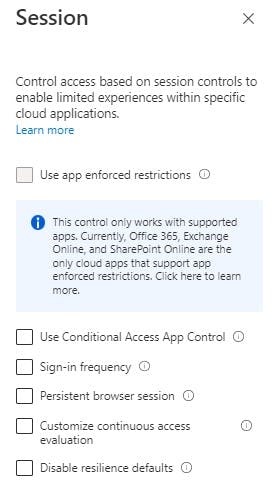
Access Controls: Session
Control access based on session controls to enable limited experiences within specific cloud applications. Not needed for this scenario so leave blank
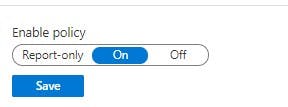
Finally we can save and enable
WARNING! - Please note there are certain scenarios with Conditional Access where you can potentially lock yourself out of your tenancy if you have NOT configured it correctly or to restrictive. Always test with report-only option so you can tweak based on results. For this scenario it is fine.
Now if the user has not yet setup MFA on their account they will be prompted to do so on first login of the Remote Desktop Client. They will need to provide a phone number or setup the mobile authenticator application on their mobile device. I have setup the mobile authenticator app.
Test sign in to AVD
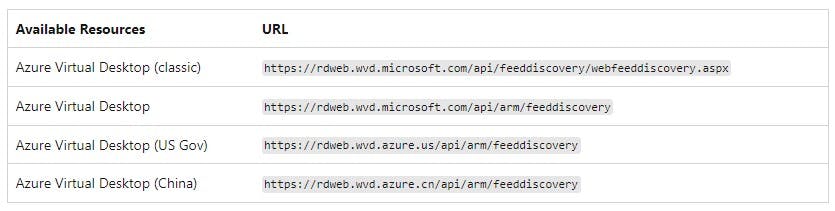
Open up you Remote Desktop Client, make sure you have unsubscribed from any accounts previously used. Select subscribe with URL as a reminder i have put them below:
Sign in when prompted with testuser1 then enter your password for the account. You will then be prompted to approve MFA request. This has been setup to go to my mobile device.
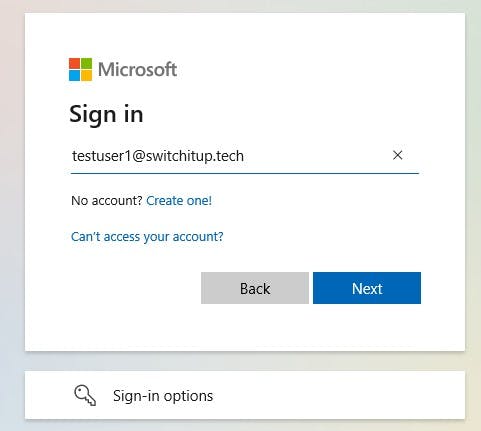
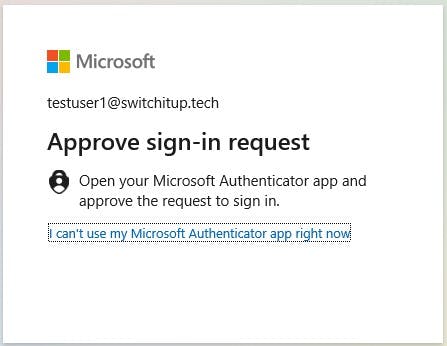
This will then sign us in to our Workspace.
Lets see how we can verify this login. Navigate to:
Azure Active Directory > Security > Conditional Access > sign-in Logs

We can further drill into this for more details:
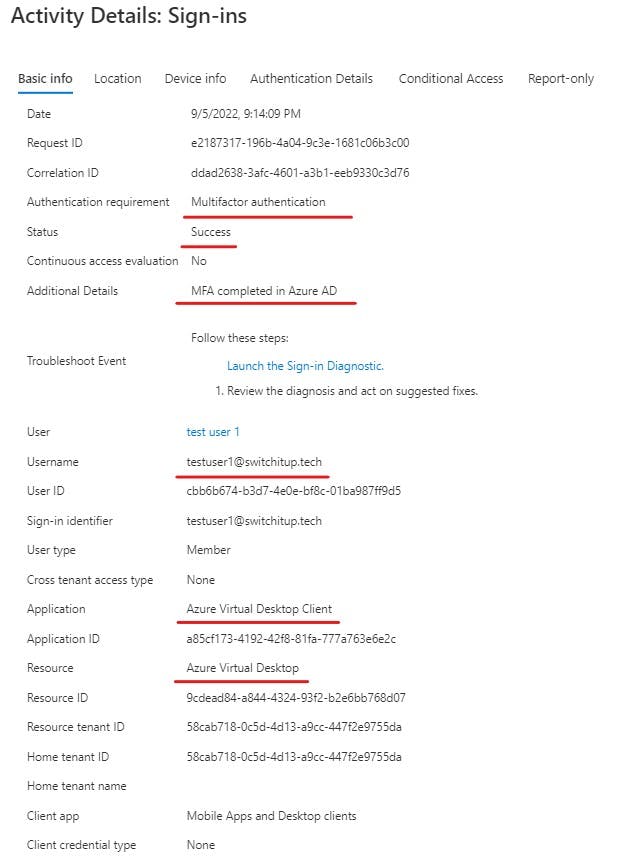
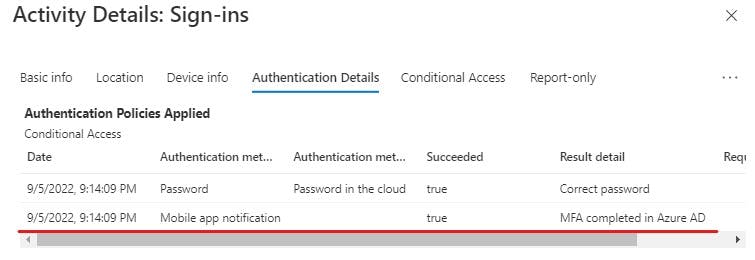
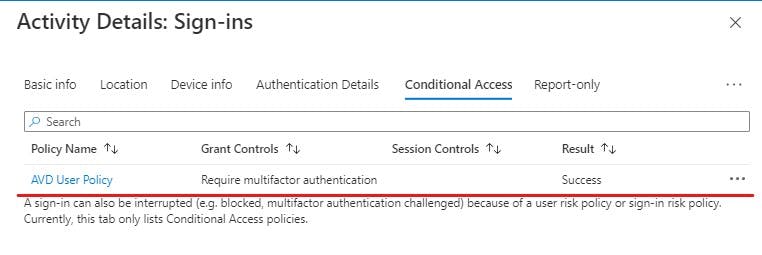
You can see the exact Conditional Access policy that has been applied to this login. This is a great way to troubleshoot your logins as it will also tell you why a login has failed and what was evaluated to get the fail.
Summary
So there we have it. We have learnt how to lock down our Azure Virtual Desktop with a conditional access policy.
IF you are a member of AVD_USERS and are accessing Azure Virtual Desktop only allow access when they have successfully verified who they are with MFA.
My next article will look at how we deal with user profiles in AVD. Traditional Local profiles will not suffice due to the roaming nature of pooled non-persistent desktops. It is recommended you use FSLogix Profile containers in your AVD environment. We will look at this in detail next time.
Thank you for Reading!
