Lets build: Domain Controller - Server Core
We will Build a Domain Controller in Windows server Core and learn how to remotely manage ADDS services.
Table of contents
Introduction:
In an ideal world, we should be deploying domain controllers on Windows Server Core. Ugh really but that's an effort there are no pretty buttons! No Thanks!
Let me finish! Powershell is not so scary when you get used to it and Server Core drastically reduces the attack vectors on your servers by essentially stripping out 90% of the GUI which can seem daunting at first.
So let's dive in and have a play with Server Core by building a Domain Controller. We will pre-stage our server with:
Name (DC01-CORE)
IP/MASK/GW
DNS Address
Install ADDS/DNS
Promote to Domain Controller
Once completed I will show you ways to manage these services via jump box using RSAT Tools.
For this I am using Windows Server 2022, to install core you will need to click Standard or Datacenter (Non-Desktop Experience).
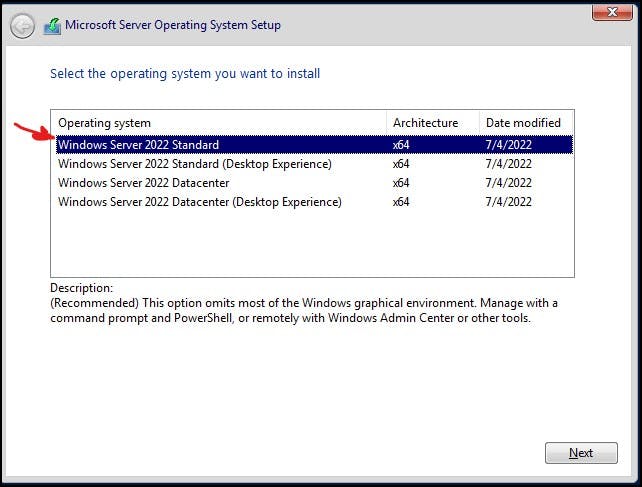
Welcome to Server Core:
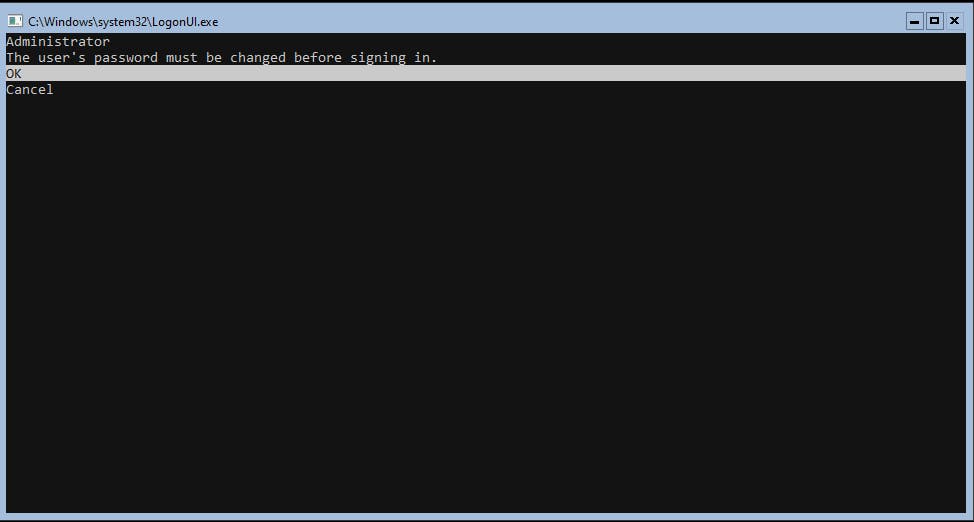
Pretty isn't it, matches my soul. when you first complete the installation you need to set a password for local administrator account. Then you will be greeted with SConfig a small menu of items you can configure with guided prompts. But whats the fun in that, we will go solo!
To close Sconfig:
CTRL+C
Open powershell to move from CMD to Powershell CMD:
powershell
To rename our machine:
Rename-Computer -NewName DC01-CORE
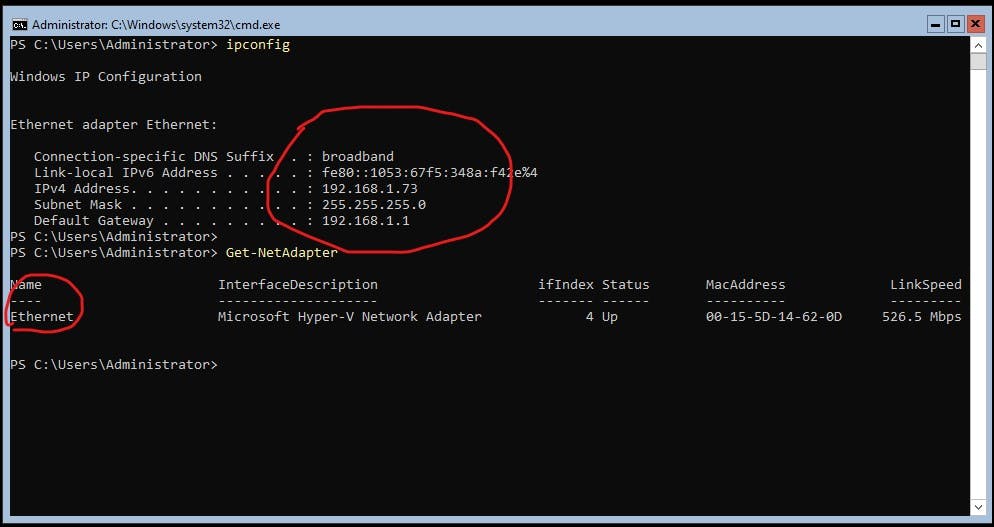
You will be prompted to restart for changes to take effect. First lets IP address the machine then reboot. My VM switch connects to my home network which has DHCP. I can verify this by using "ipconfig" to see the address it has picked up. My VM also has a single NIC where th alias = Ethernet.
ipconfig
Get-NetAdapter
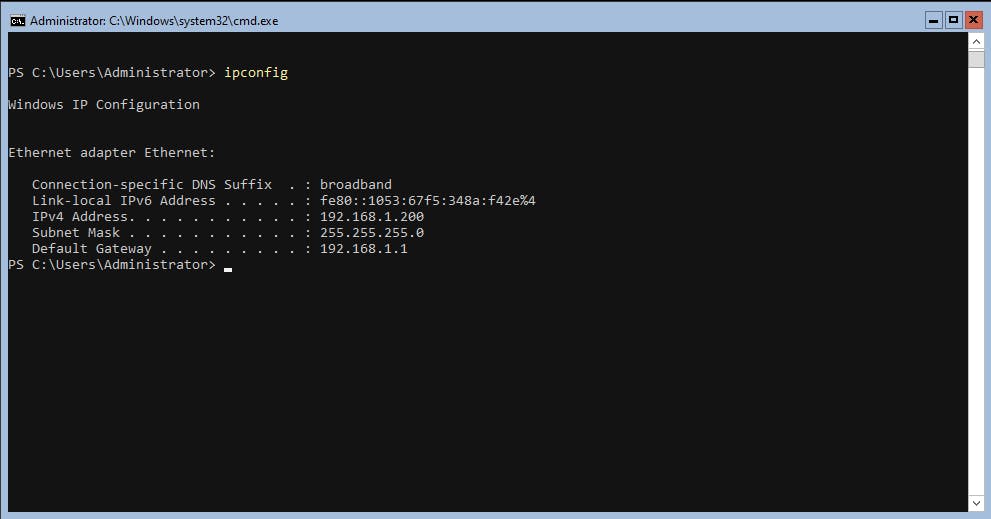
let's change my IP to 192.168.1.200, Prefix Address: 255.255.255.0 (24), Default Gateway: 192.168.1.1
New-NetIPAddress -InterfaceAlias Ethernet -IPAddress 192.168.1.200 -PrefixAddress 24 -DefaultGateway 192.168.1.1
Verify with ipconfig
Lets now add a DNS address for a resolution to itself and my home router as secondary
Set-DNSClientServerAddress -InterfaceAlias Ethernet -ServerAddresses 127.0.0.0,192.168.1.1
Verify configuration with ipconfig /all (this will also show DNS settings)
Let us restart the server for the name to take effect:
Restart-Computer
Close Sconfig with CTRL+C again and run powershell on reboot
Let's now install ADDS/DNS
#Verify Windows Features + names
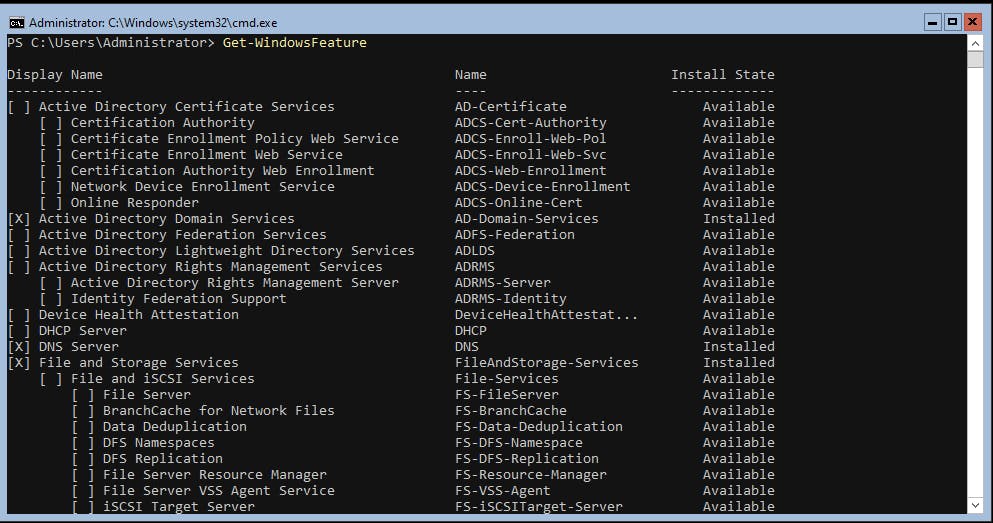
get-WindowsFeature
##Install ADDS and DNS
Install-WindowsFeature AD-Domain-Services, DNS -IncludeMangementTools
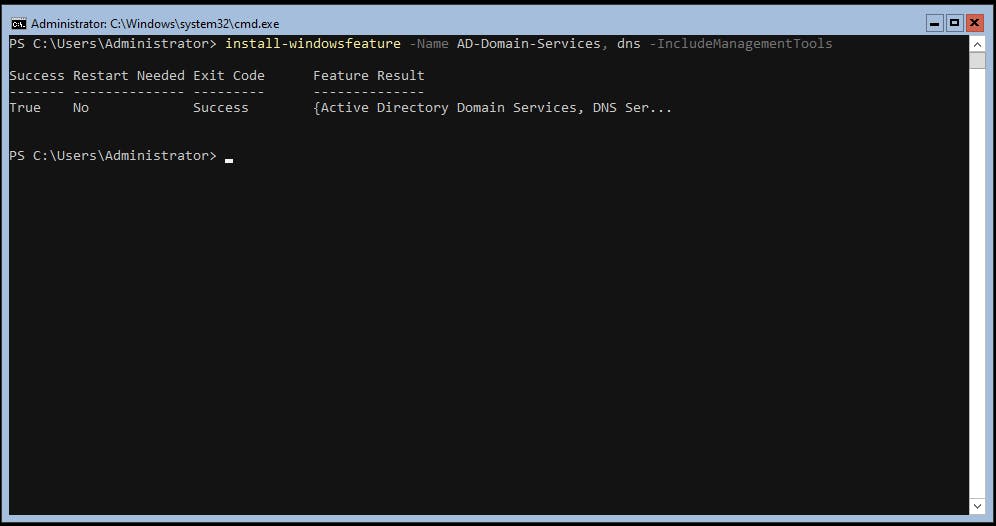
The Get-Windows Feature can also be used to verify what is installed:
Let's now Promote the server to a Domain Controller, as this is our first and only ADDS server we will need to also create the Forest/domain during the process.
Install-ADDSForest -DomainName switchitup.tech -InstallDNS -DomainMode WinThreshold -ForestMode WinThreshold
-DomainName = What you want your ADDS Domain to be
-InstallDNS = default value = True will install DNS zone into the DNS service
-DomainMode = 2008-2016 (2016 is the highest, also known as "WinThreshold")
-ForestMode = 2008-2016 (2016 is the highest, also known as "WinThreshold")
On hitting enter you will need to supply a DSRM Password (Directory Services Recovery Mode Password) you will then be asked if you wish to reboot to finish the promotion. When Sconfig loads we can see we are now a Domain Joined Machine:
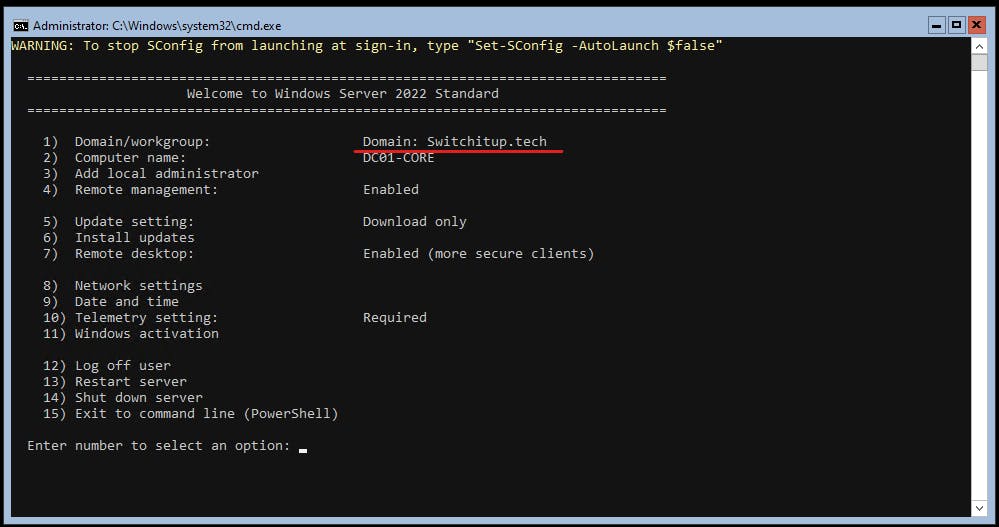
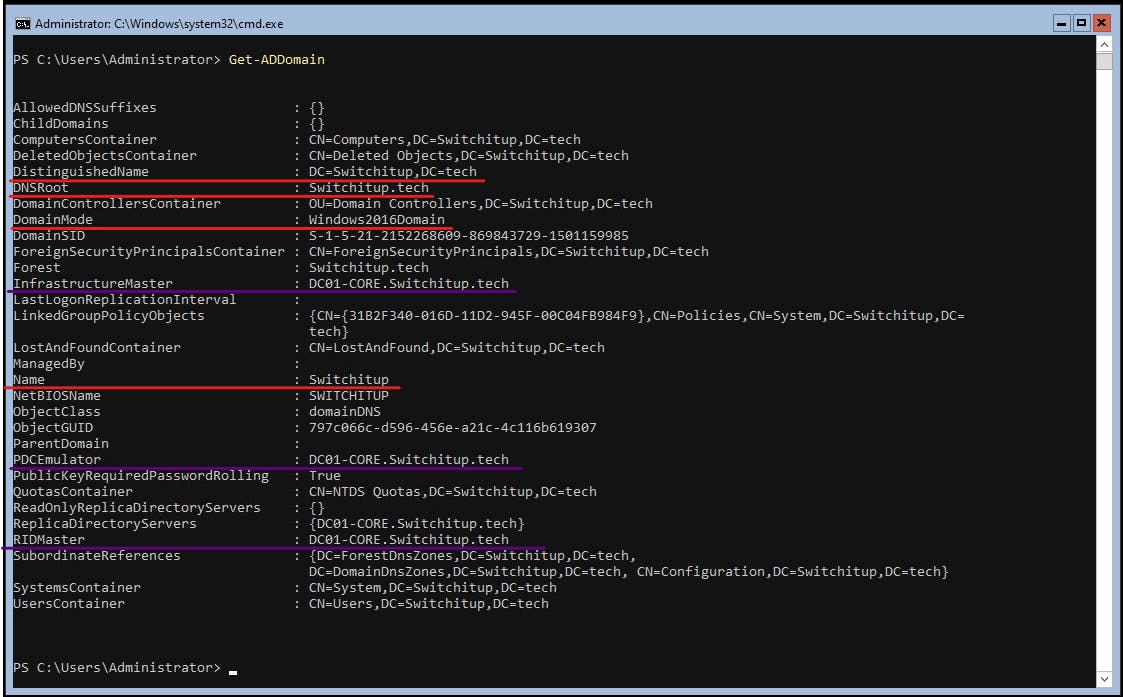
We can verify the Forest and Domain setup using the following:
Get-ADDomain
Get-ADForest
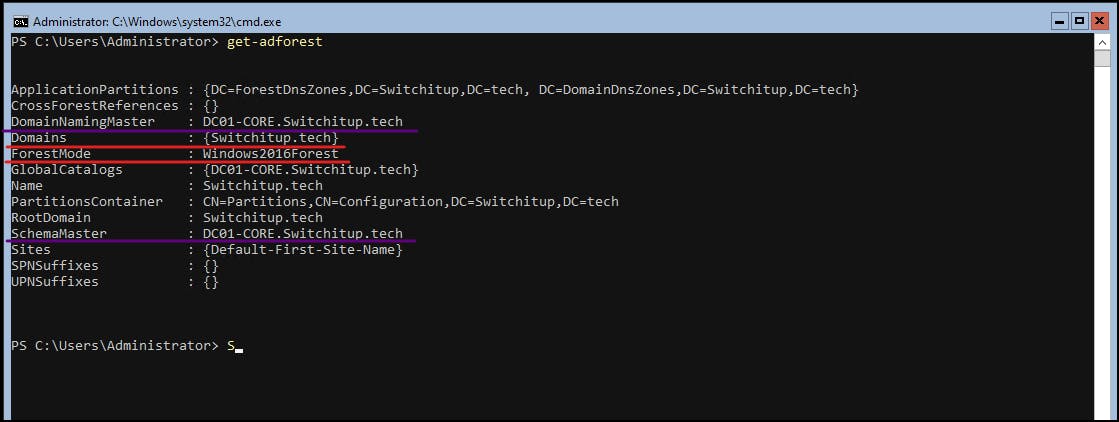
Red = Variables we applied to create our domain
Purple = Domain FSMO Roles (For more information on these critical domain roles and what they do check out my FSMO Article here:
https://switchitup.tech/managing-active-directory-fsmo-roles
So how can we get to Active Directory Users and Computers Console to manage AD objects? Well, you can use Powershell OR you can revert to the GUI via a remote machine using RSAT tools if you are on a Windows client OR if you have a Windows server with a GUI you can manage it via server manager remotely.
Server Manager
I have joined a second Windows Server 2022 box to my new domain and we will remotely manage ADDS via Server Manager:
Select Manage > Create Server Group:
Name your group and search for the core server we created:
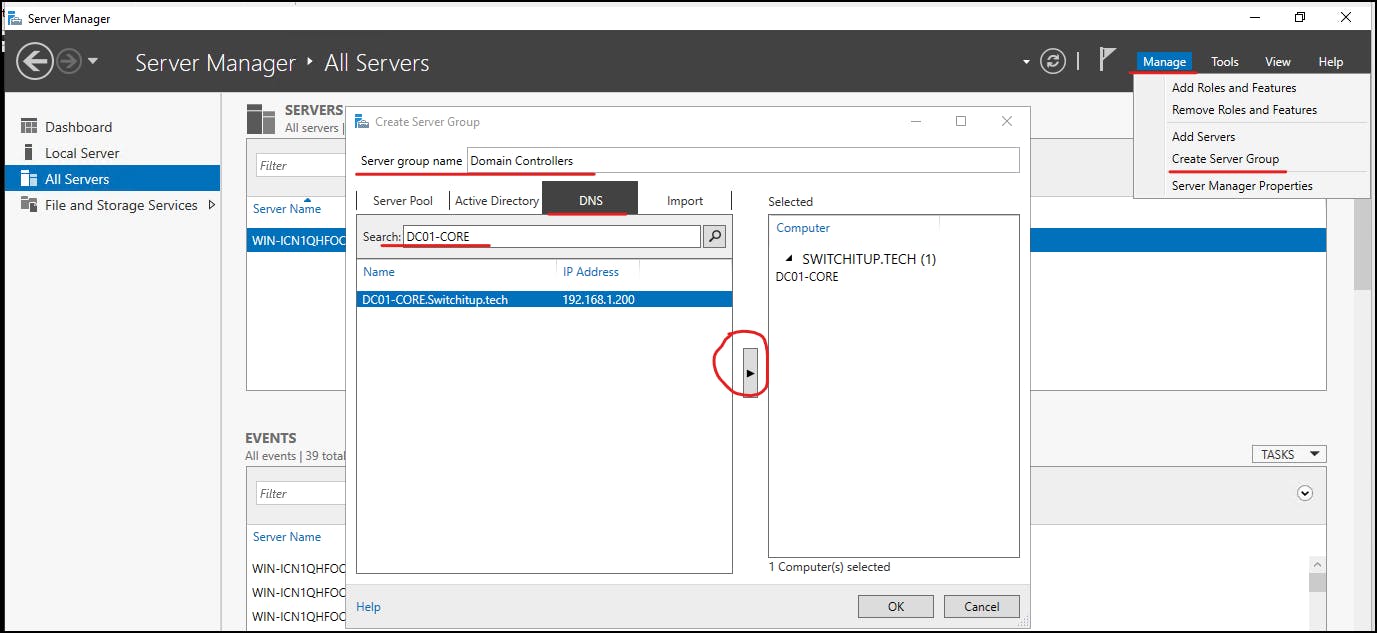
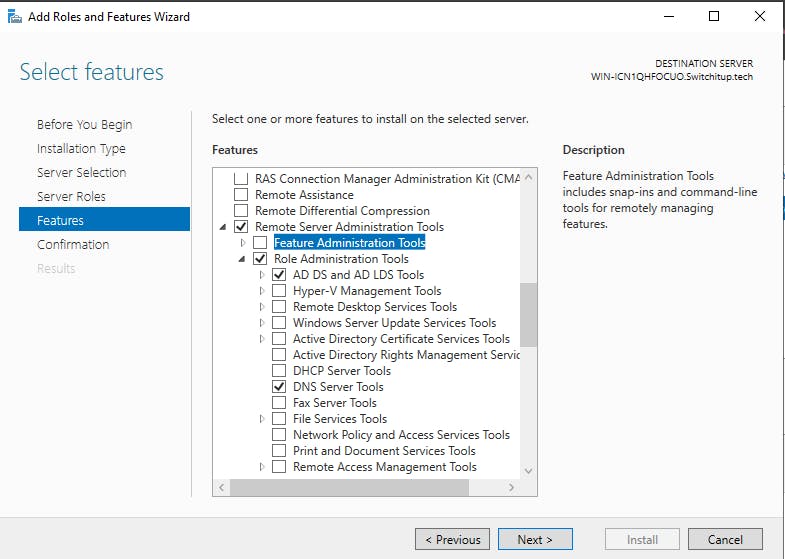
We now need to install the admin tools for ADDS and DNS to manage these services remotely:
Once installed open up Active Directory Users and Computers from the Tools Menu in Server Manager:
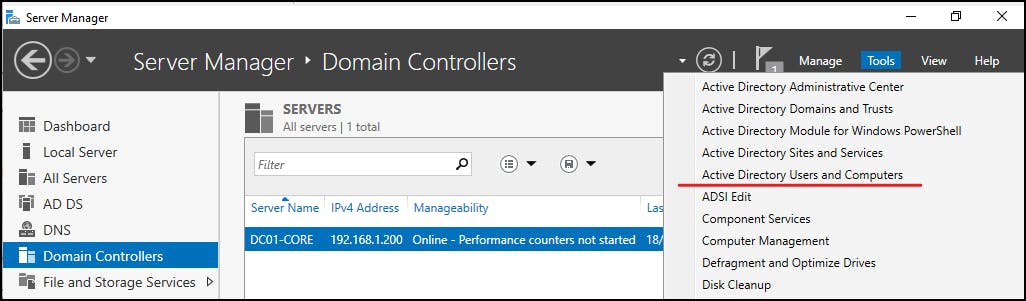
Below I have created some Organisational Units and a User (myself) as a domain admin member:
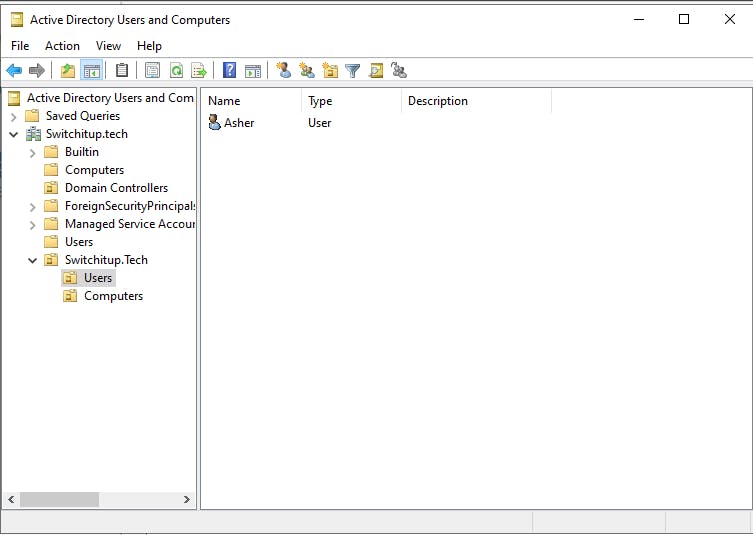
Lets verify and run the DNS tool, connect to our server core machine:
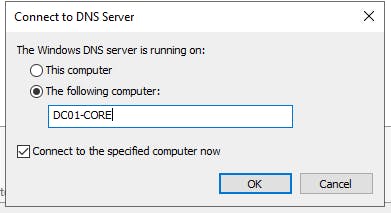
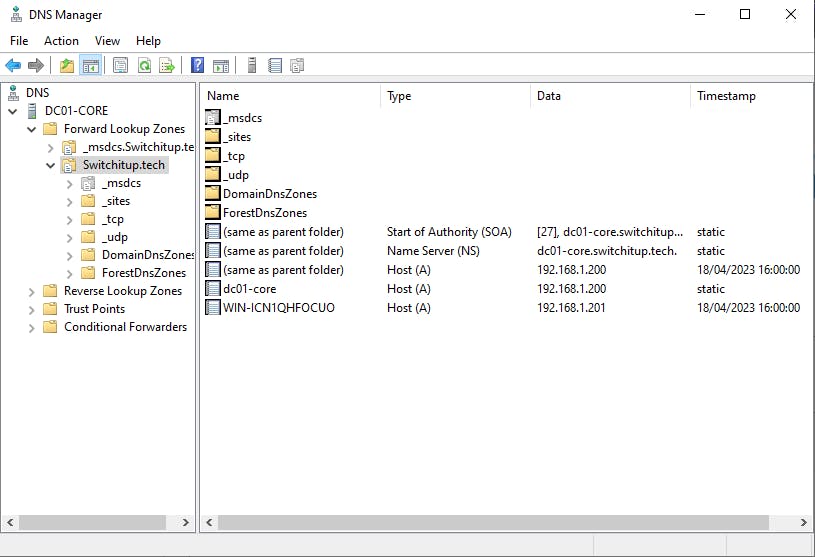
You can make changes to your DNS via the GUI tool remotely.
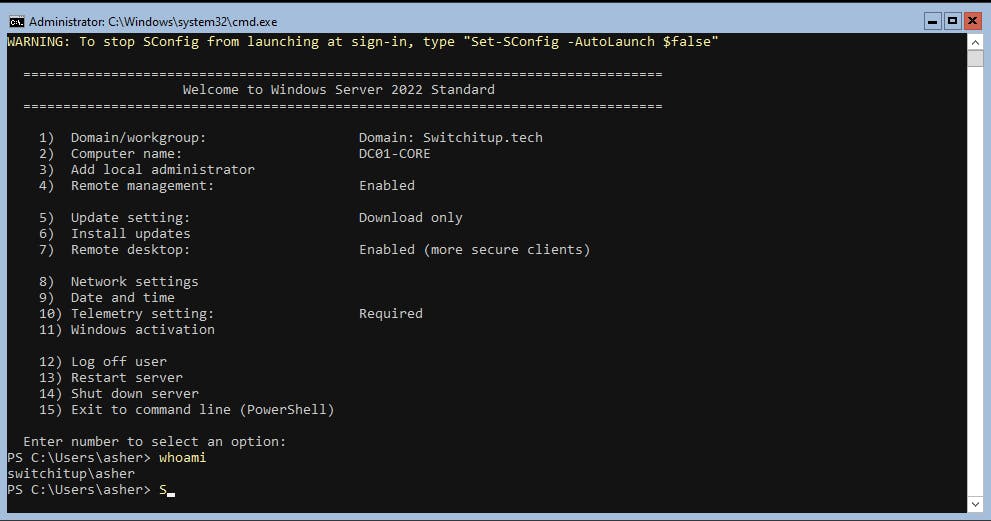
Let's logout off our Server Core machine and log in as Asher to verify the user is created:
Type Sconfig to get the menu back up and type 12 for "log off user". After a Control+Alt+Del hit ESC to login as a new User:
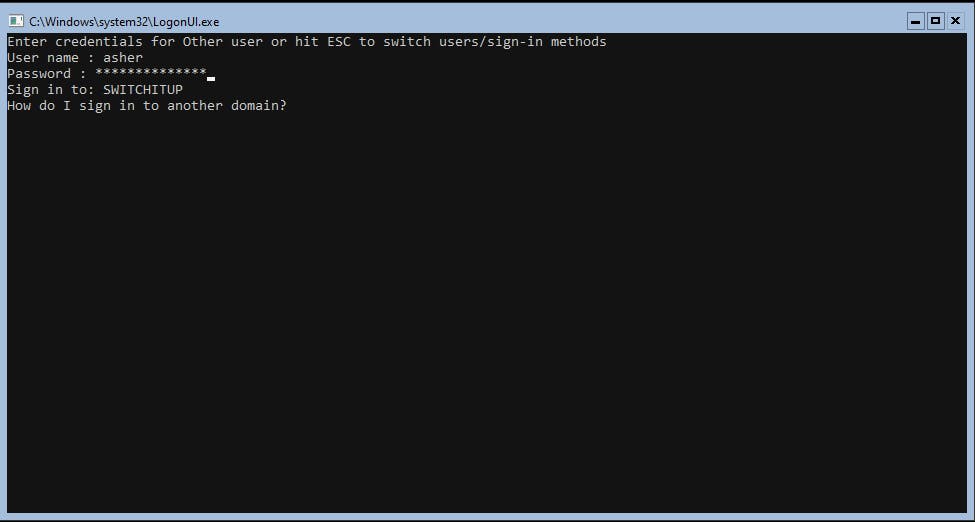
Type "whoami" to verify the user logged in.
Summary:
There you have it we have created a new Domain Controller and forest on Server Core and learned how we can use server manager to remotely configure and access Active Directory via the usual GUI tools. This also reduces the attack surface of your Domain Controllers. To get similar tools on Windows Client you can add RSAT tools via Additional Windows Features in the control panel add and remove programs.
