In this post we look at setting up Single Sign-On (SSO) between your Azure Active Directory tenant and your Google Workspace/Cloud Tenant.
I Recently completed this work for a customer that was using on-premise Active Directory Federated Services (ADFS). We wanted to remove ADFS from the environment completely however, the consequence of this meant single sign on with their Google accounts would break. So what better then to move this functionality to their existing Azure Tenant.
Assumptions of This Article:
- A Global Administrator account to an active Azure AD Tenant
- A Google Administrator account to an active Google Tenant
- You have Configured users that exist in both tenants
- Everyone can use SSO to access Google (Nothing locked down by Groups/Individuals)
- Nothing fancy like Conditional Access
Objectives:
- Create the Enterprise Application in Azure Active Directory (Azure)
- Configure the SAML settings for the G Suite Connector (Azure)
- Configure Attributes and Claims for the G Suite Connector (Azure)
- Download the SAML Signing Certificate (Azure)
- Configure Google SSO Identity Provider (Google)
- Test Access
Create the Enterprise Application in Azure Active Directory
Login to your Azure Active Directory Tenant and navigate to the following:
Azure Active Directory > Enterprise Application > New Application

Type in the search "Google" and the connector will appear

When selected, the Application will then appear in your list of current Enterprise Applications. The next stage is to provision the SAML settings for the app we just added.
Configure SAML Settings for the Azure G Suite Connector
Click on your newly created G Suite Connector from your list of current Enterprise Apps. If you have a lot of apps you may need to use the search box. On this page we then want to select "Setup Single Sign-on" followed by "SAML"
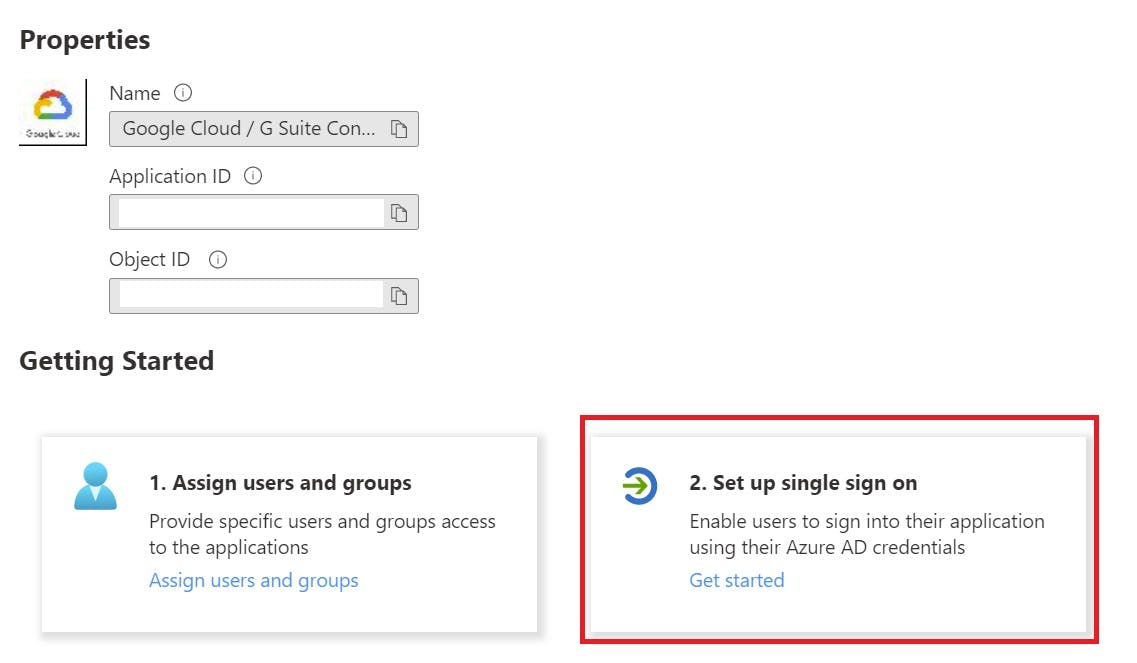
You will need to configure the following settings below, Please note, you will need to change <Primary Domain> in Sign-on URL to your primary Google Domain!
- Identifier (Entity ID) =google.com - Reply URL =
https://google.com/ - Sign-on URL =
https://google.com/a/<primary Domain>/servicelogin?continue=https://console.cloud.google.com After completing the relevant fields the SAML settings should look like the following below:
Now we can move on to Attributes and Claims.
Configure Attributes and Claims for the Azure G Suite Connector
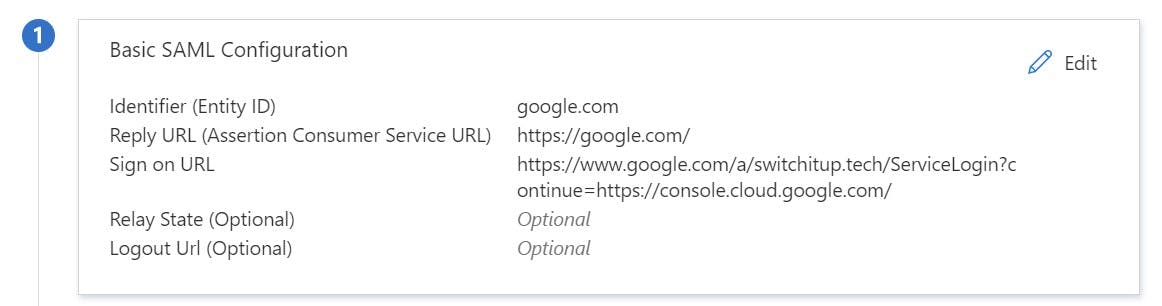
Below "Basic SAML Configuration" you will see "Attributes and Claims", You will want to remove all "Additional Claims" but leave the "Required Claim" as Unique User Identifier (Name ID) = User.userprinciplename [nameid-format:emailAddress]. You should end up with the below result.
Download the Azure SAML Signing Certificate
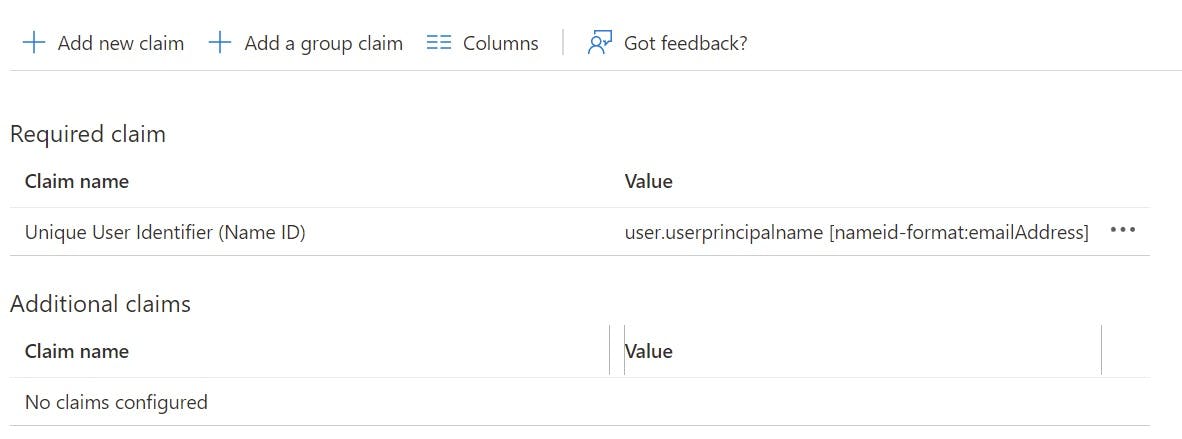
Below "Attributes and Claims" you will see "SAML Signing Certificate". You will need to download this (Base64) certificate to later apply to your Google SSO Setup. The certificate will be used as part of the authentication process between both tenants. Hit Download and save in a location for later.
Please note these certificates do have a validity date before expiration which, can be seen in "Expiration" on "SAML Signing Certificate" settings. I have removed my settings for security purposes in the above image. Once the certificate expires you will need to re-download and replace the certificate on the Google Tenant for SSO functionality to resume.
Configure Google SSO Identity Provider
log into your Google Tenant and navigate to the following:
Security > Authentication > SSO With Third Party IDP > Add SSO Profile
You need to provide the following:
SSO Profile for your Organisation = ON
Sign-in Page URL = login URL found on the Azure SSO Settings for G Suite Connector
Sign-out page URL = https://login.microsoftonline.com/common/wsfederation?wa=wsignout1.0
Use a domain-specific Issuer = OFF
Change Password URL = https://account.activedirectory.windowsazure.com/changepassword.aspx
The login URL can be found on the G Suite Connector SSO settings page ( I have omitted part of mine for security purposes). Copy this link from Azure into Google. The below Image shows where to find the link:
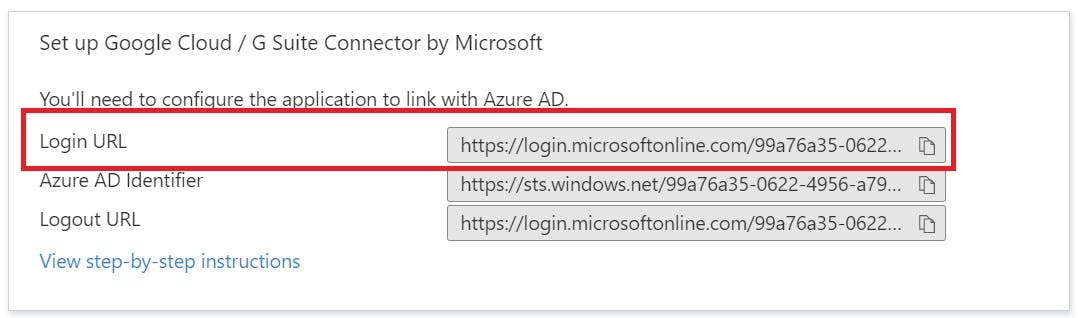
Copy the "Login URL" on Azure to the "Sign-in Page URL" in Google SSO profile:
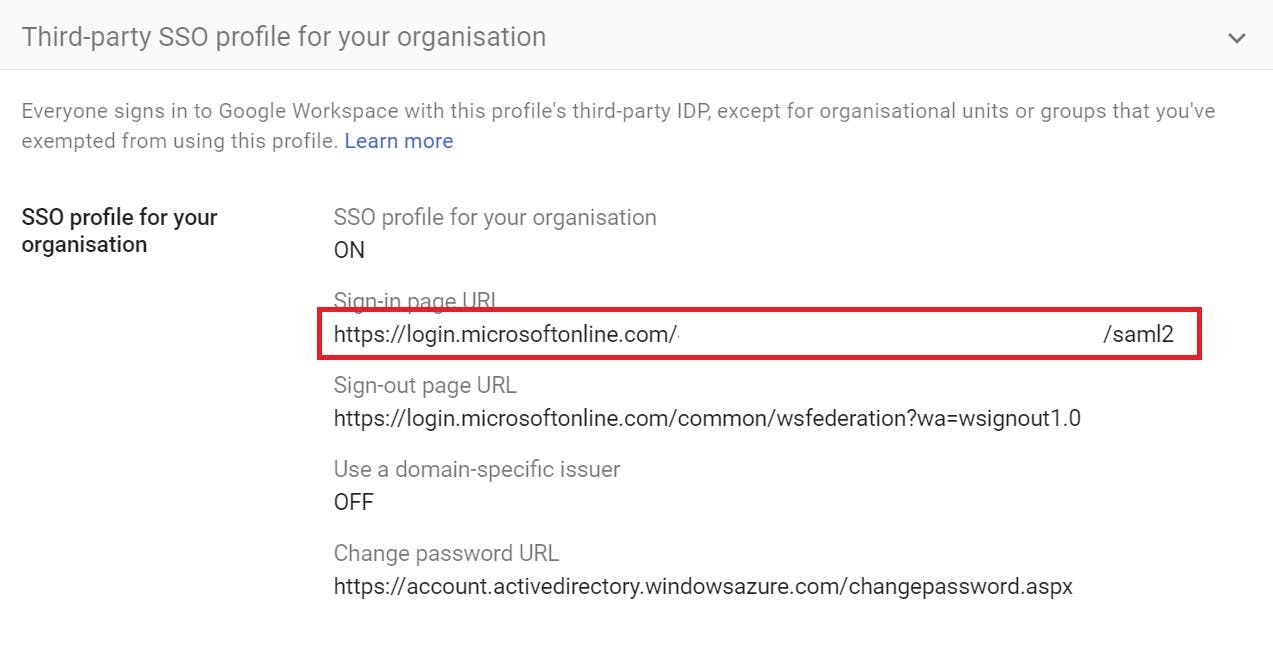
Finally, you need to upload the Certificate you downloaded earlier from Azure and apply it to the SSO profile. You can do this with the link provided in the profile settings.
Test Google SSO Access
There are a number of ways you can test SSO.
First method is via your browser by logging into your google account, you will then be forced to sign-in with your Azure Active directory Account.
Second Method is to navigate to the Single Sign-on settings of your G Suite connector app, here you will find a test option where you can test SSO as a specific user, this will however require a web browser extension in Chrome/Edge. This option is more granular because it provides troubleshooting on the Azure side and can offer insight into why SSO isn't working for an individual and guide you to a resolution.
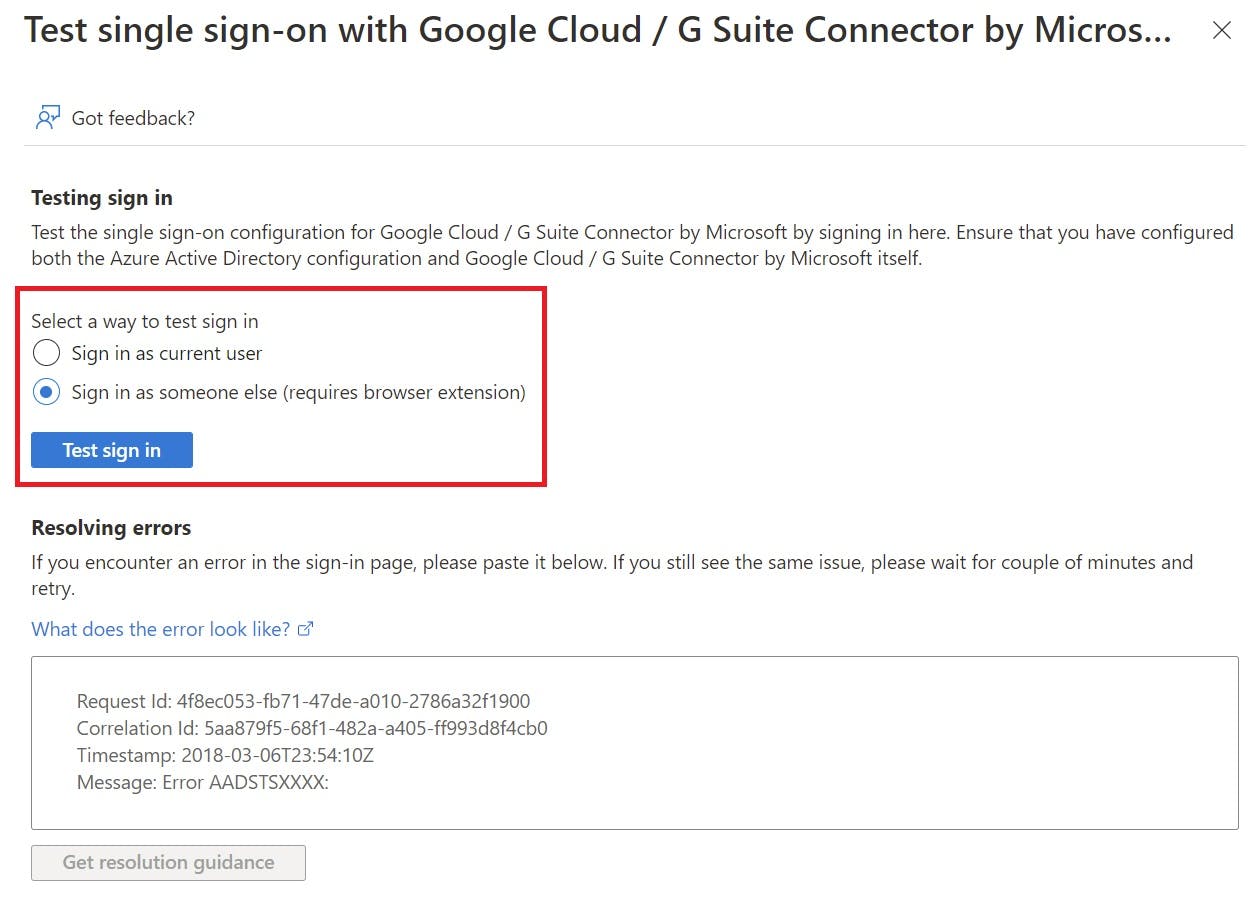
The example in this post has assumed all users can use SSO to log into Google without any restrictions. Based on this, we need to make sure in the "Properties" settings of the G Suite Connector App that "Assignment Required" is set to NO:

If "Assignment Required" is set to YES, you can lock SSO and access to Google down by Security Groups or Individual users by navigating to:
Azure Active Directory > Enterprise Applications > Google Cloud / G Suite Connector by Microsoft > Users and Groups > None Selected
Congratulations, You have now configured SSO between your Azure and Google Tenants.
Hit me up in the comments section on how you found this guide. I'm always looking for feedback on how to make my articles better.