Introduction:
A customer request has come in to link two Azure tenants together as a result of an acquisition. They wish to use Azure B2B Direct to create trust between each Azure/365 tenant.
Customer request:
Want the Tenants to remain separate but access to be given to resources both ways
Want to use Teams Shared Instances
Want External users visible in the GAL (both tenants)
So this topic got a tad confusing as when you configure External Identities it looks like it asks you to configure all B2B types (Collaboration/Direct) which isn't the case, you select the scenario you require.
We again confused ourselves with this whole process because when we tested it in Dev we first configured B2B Direct, expected to see external users appear in each tenant, scratched our heads as to why they didn't initially appear, then configured cross-tenant sync thinking it was part of the B2B Direct process. This is not the case, Cross sync achieves a completely separate goal.
What Tenant-Sync gave us were the GAL requirement and collaboration features so it all wasn't in vein (this will be covered in a second post as to not confuse).
B2B Direct
creates a trust between tenants. The users stay in their tenants but get access to Teams shared channels. This means users from either tenant (based on inbound and outbound settings and Teams policies) can create a channel and invite colleagues from the external tenant to work in the team without having to switch between two different companies (directories) in teams.
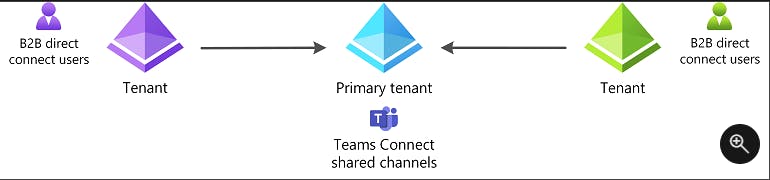
Here's the primary constraint with using B2B direct connect across multiple tenants:
- Currently, B2B direct connect works only with Teams Connect shared channels.
B2B Direct - Setup
Log into the Azure Portal and navigate to:
Azure Active Directory > External Identities > Cross-Tenant Access Settings
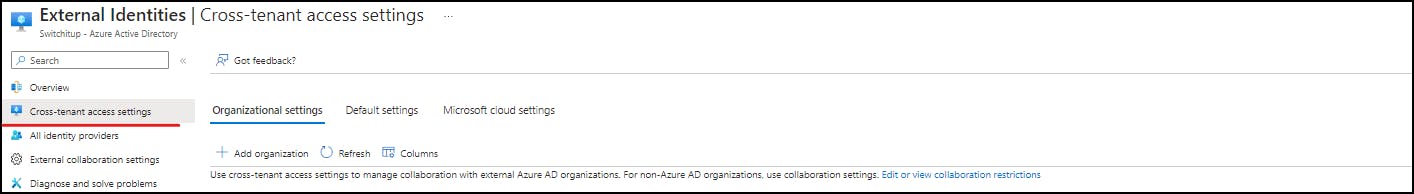
Select: "Add Organization" which will bring up the wizard on the right-hand side. Here you can enter the External Tenants ID. Once entered it should automatically find the tenant Name - in my instance this is "NeilLab"
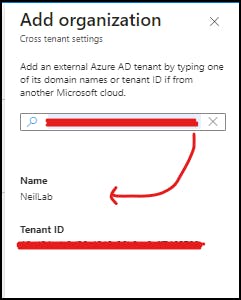
Once added we can configure the Inbound and Outbound Settings for the tenant
Inbound - restrictions for external users accessing your tenant
Outbound - Restrictions for your users communicating with the external Tenant.

Inbound Settings
Select "Configure" on "Inbound Settings" and you will be greeted with several categories:
B2B Collaboration (N/A here)
B2B Direct Connect
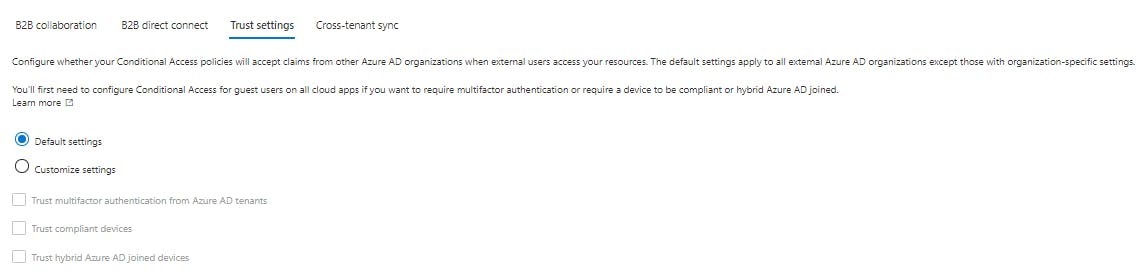
Trust Settings
Cross-tenant Sync (Allows External admins to sync users into your tenant)
You don't need to configure all of these, configure what suits your access requirement scenario.
We have discussed B2B Direct but let's quickly touch on the other options:
B2B Collaboration Settings - Allow users to be invited to the tenant and added to your tenant as guests.
Trust settings - Allow and trust the authentication tokens from the external tenant for users that have authenticated in their tenant against your conditional access policies. criteria include:
Trust MFA
Compliant Devices (Intune compliance)
Trust hybrid Joined devices
Cross-tenant Sync - Allows the external admin to provision (push) required users into your tenant, they will appear as external users and will be added to your Exchange Online "Contacts". This gives you more granular automated approaches to managing external identities in your tenant. You can then also lock applications down with conditional access policies applied to these users as an example.
You can view the B2B default settings back on "Cross-tenant Account settings"
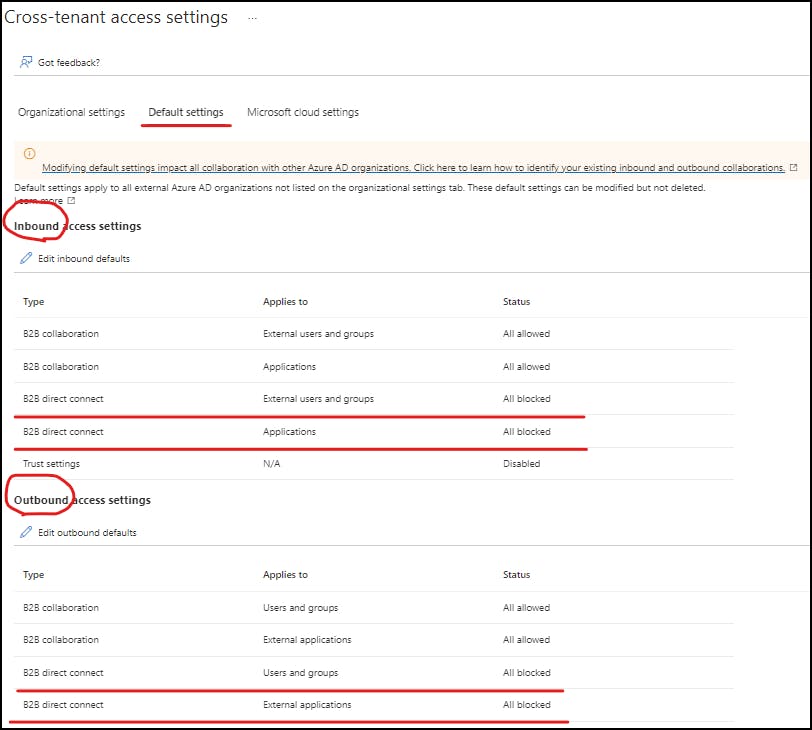
Disclaimer:
Editing these settings impacts B2B Collaboration with all AD Organisations. Edit with Caution.
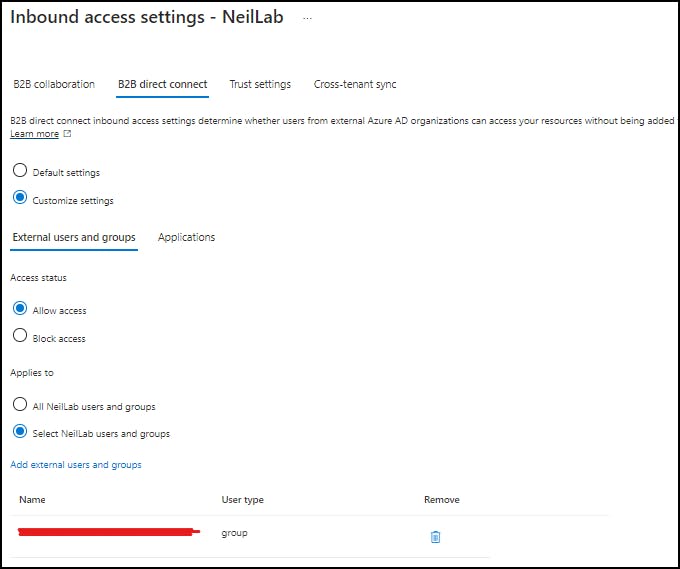
As we want B2B direct we will start there, we are going to customize this section to "Allow Access" applies to "Select NeilLab Users and Groups" Some businesses may want everything open by default but if you have security concerns or just want a limited number of users to be trusted you can lock this down to users/groups. Neil has created a group called B2B-Switchitup in his tenant and provided me with his object ID for this group.
Select "Add External Users and groups" to add the object GUID - THIS IS THE GROUP IN THE EXTERNAL TENANT
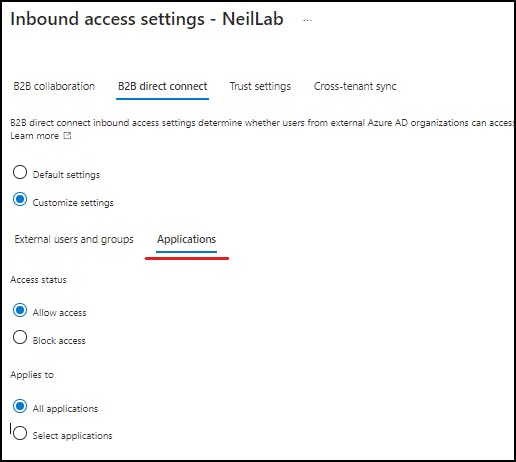
Select the "Applications" tab set "Access Status" to "Allow Access" and "applies to" "All applications". Again you can lock this down to your choosing.
Trust settings will be left as default and "Automatically redeem invitations with the Tenant <Name>" Enabled:
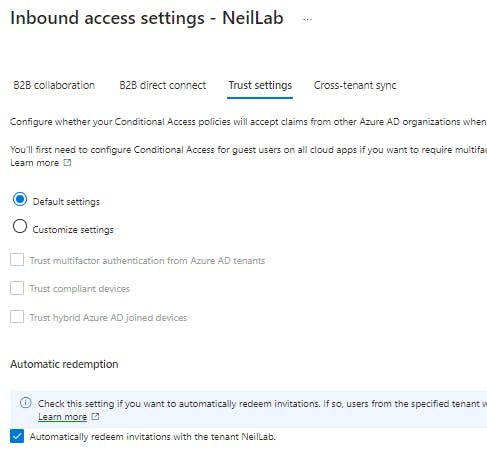
Automatically Redeem Invitations with the tenant <Name>:
Check this setting if you want to automatically redeem invitations. If so, users from the specified tenant won't have to accept the consent prompt the first time they access this tenant using cross-tenant synchronization, B2B collaboration, or B2B direct connect. This setting will only suppress the consent prompt if the specified tenant checks this setting for outbound access as well.
Outbound Settings:
outbound settings are very similar to the inbound, again we will configure B2B Direct and leave Trust settings at default.
- Customize Settings
User and Groups
Access Status = Allow Access
Applies to = Select Switcitup users and Groups
External Applications
Access Status = Allow Access
Applies to = All External Apps
I have created a group in AAD called "B2B-NeilLab" and added this to the users and groups section in the outbound settings
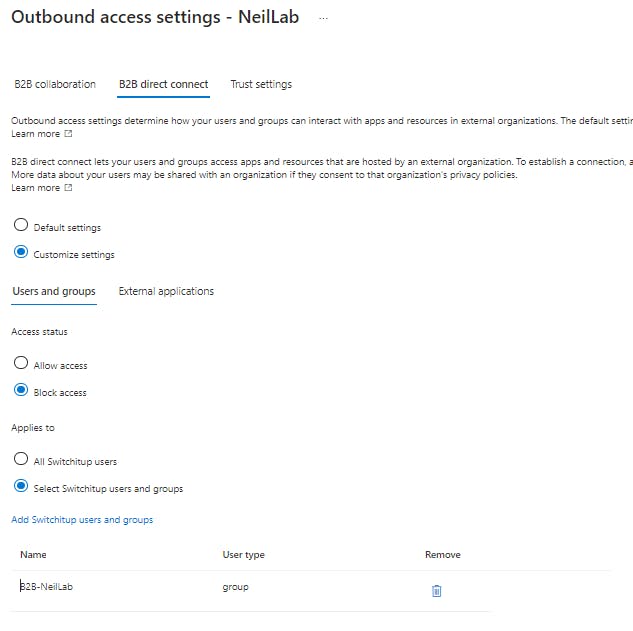
External Tenant Setup
The external administrator needs to set up the collaboration settings on their side. These don't necessarily have to match, as you could have a one-way trust. So you could effectively block access in a single direction. But for this scenario, we will keep everything open in both directions.
Teams Shared instances
As noted earlier B2B Direct gives you the capability to use Teams Shared Instances. Let's quickly look at how this is set up and controlled. First, we need to log into the Teams admin portal and navigate to the following:
"Microsoft Teams Admin Centre > Teams Policies"
By default you should see "Global (Org-wide default) policy", click on this to edit.
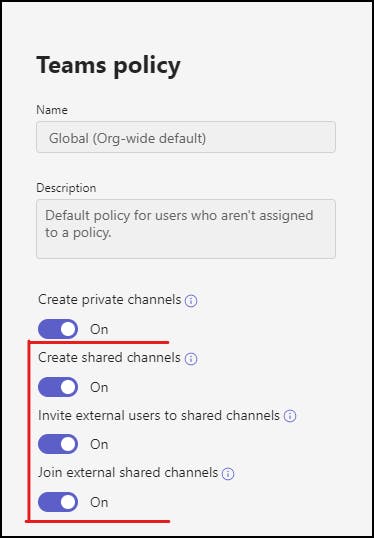
Make sure the following options are selected. You can make another policy and lock this down to individual users or groups if you want these options restricted.
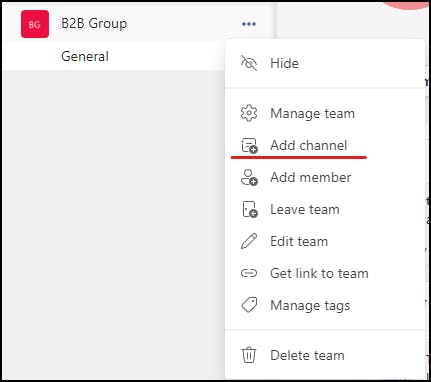
Now, in Teams, we are going to create a new team called "B2B Group"
click on the "..." by your team name to create a channel with "Add Channel"
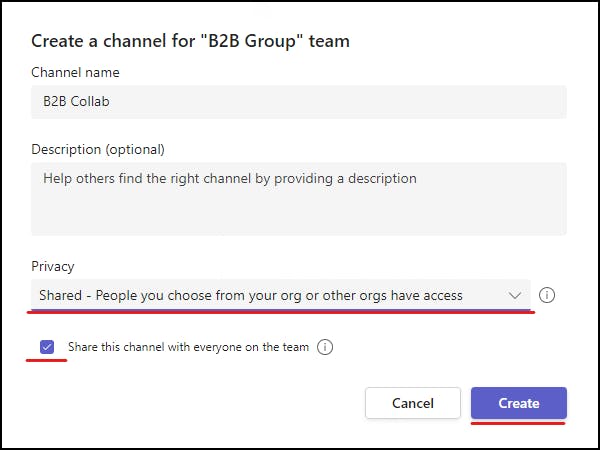
From the wizard, you need to change the Privacy to "Shared - People you choose from your org or other orgs have access"
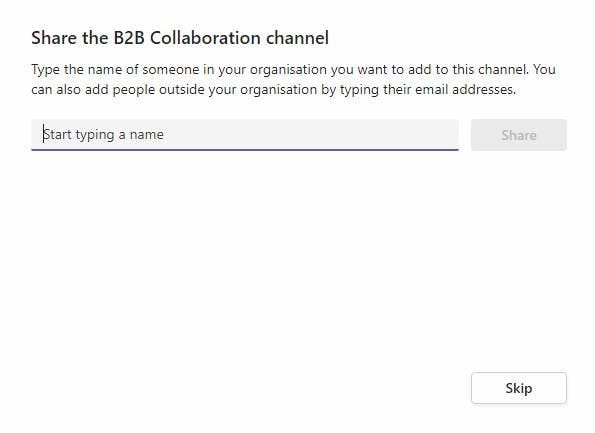
The next step is to add your users to the channel, if your collaboration settings are all correct as per this article, you should be able to add users from the external organization.
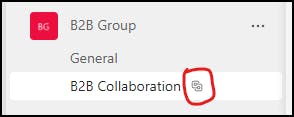
Notice the link next to your new channel to show it's shared:
Summary
There we have it B2B Direct for Teams Shared instances and how to implement and manage these instances from a glance.
Once again thank you for the Read.