Recently had a customer wanting to remove Active Directory Federated Services (ADFS) from their on-premise environment.
"Active Directory Federation Services (AD FS) makes it possible for local users and federated users to use claims-based single sign-on (SSO) to Web sites and services. You can use AD FS to enable your organization to collaborate securely across Active Directory domains with other external organizations by using identity federation."
docs.microsoft.com/en-us/windows-server/ide..
The customer currently uses AD Connect to sync their on premise AD into Azure Active Directory and it is set to use federation via their AD FS. (we will cover this later)
For those of you unfamiliar with AD Connect it is a sync tool that allows for Hybrid deployments between your on Premise Active Directory (AD) and Azure Active Directory (AAD).
It's not often I see AD FS still being used, making AD Connect with Federation also rare. It tends to only be implemented in organisations that already make use of it from years before. To deploy AD Connect with federation can be costly and complex based on the required infrastructure on-premise. This is far beyond the scope of this blog post because I'm more interested in tearing it down. but check out the link below if you are curious:
docs.microsoft.com/en-us/azure/active-direc..
Obviously tearing down ADFS will break their current federated sync with Azure Active Directory. We agreed as part of tear down to move Federation to Password Hash Sync.
Lets quickly review 3 of the main sync methods we can utilize with AD Connect:
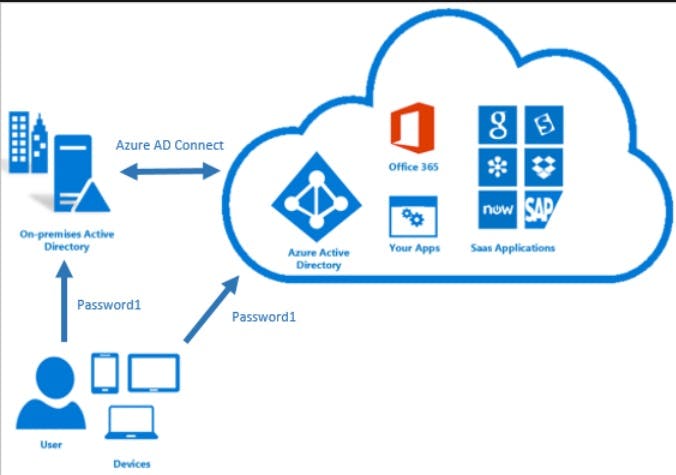
Password Hash Sync (PHS)
Probably the simplest and most common used method
Syncs the hash,of a hash, of the users password from AD to Azure AD
Users use the same password to login to their Microsoft cloud services as their on-premise account
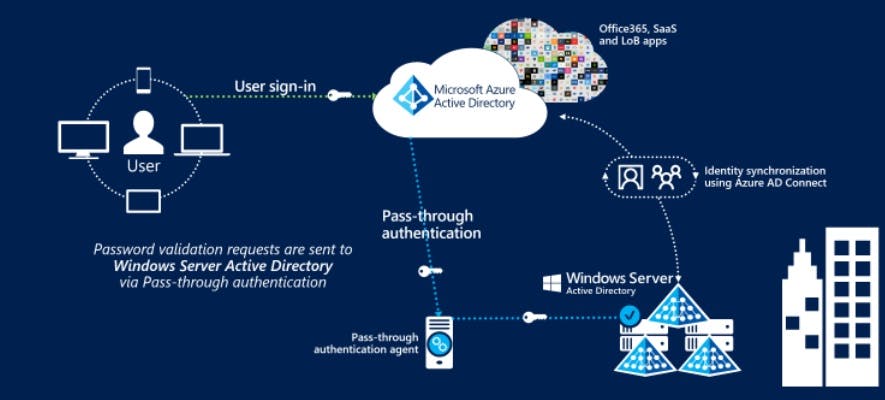
Pass-thru Authentication
Great for companies that have on-premise password/security policies they want to use with the cloud
requires a lightweight agent on-premise
same benefits as PHS
A Few CONS
Cant login with a temporary/expired password
Can't use AD Connect Health
Needs PHS enabled on tenant to function (Effects Azure Domain Services)
Does not apply to cloud only users, users must be synced with AD Connect.
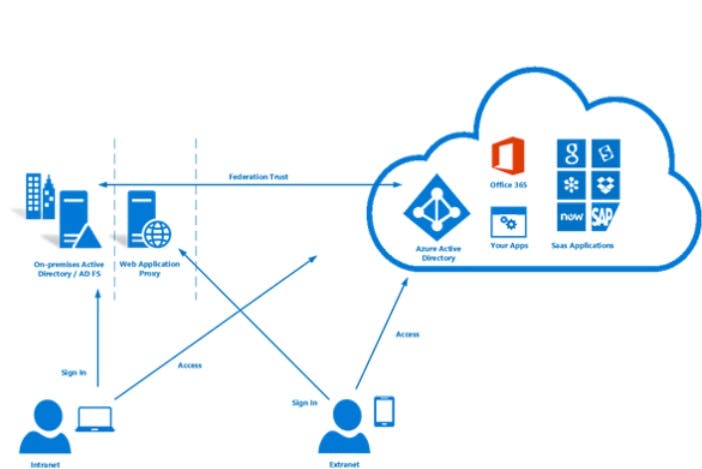
Federation
Leverages your on-premise ADFS infrastructure
Allows Federated Single Sign-on (SSO)
longer setup process to integrate all parts
Configuration
So first of all can I move from Federation to Password Hash-Sync? The answer is yes you can and it's not that complicated as a bonus. It involves changing the settings in AD Connect and a GPO. Lets take a look:
Objectives
Enable PHS in AD Connect
Change user Sign settings to PHS + SSO in AD Connect
Create GPO to create intranet zone link for SSO
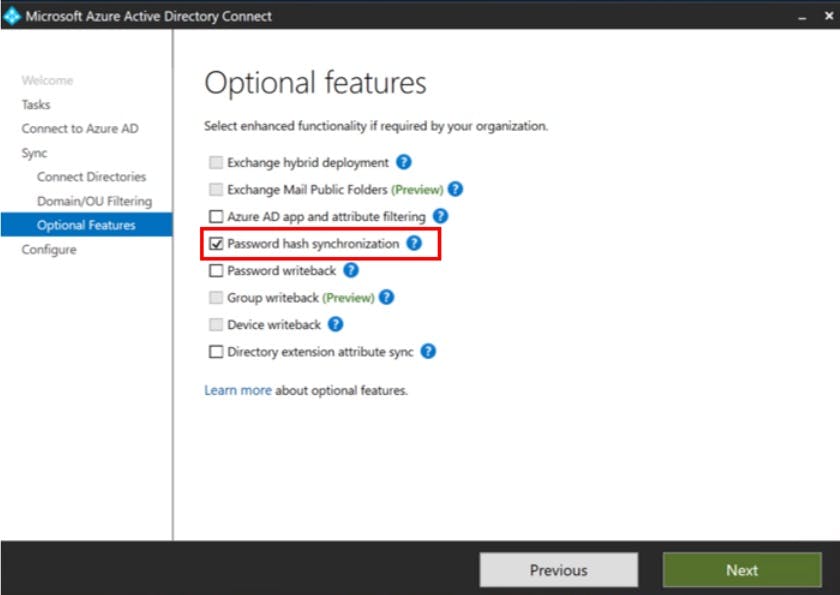
Enable PHS
Open AD Connect: Configure > Customize Synchronization Options > Input global admin username and credentials > Next > Next > Optional Features screen select Password Hash Sync > Next > Configure
now we can change the user-sign in settings to Password Hash Sync and enable SSO:
Change user Sign-in Settings
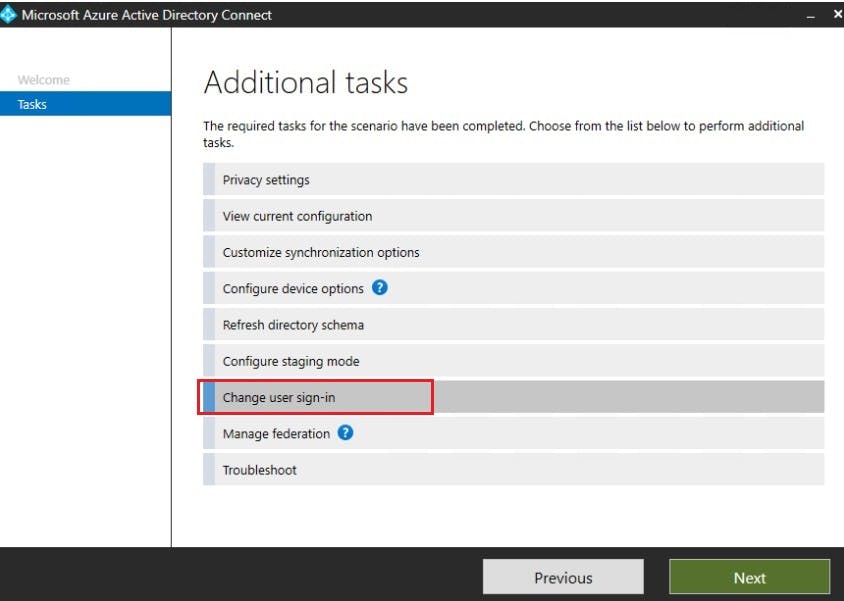
We will then connect to your Azure AD Tenant using global administrator account:
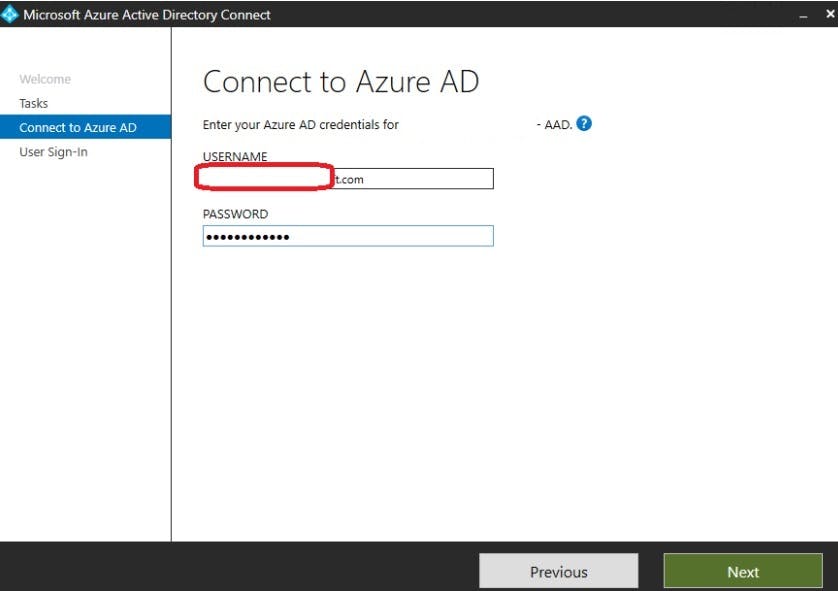
Change sign-in to use PHS rather then Federated:
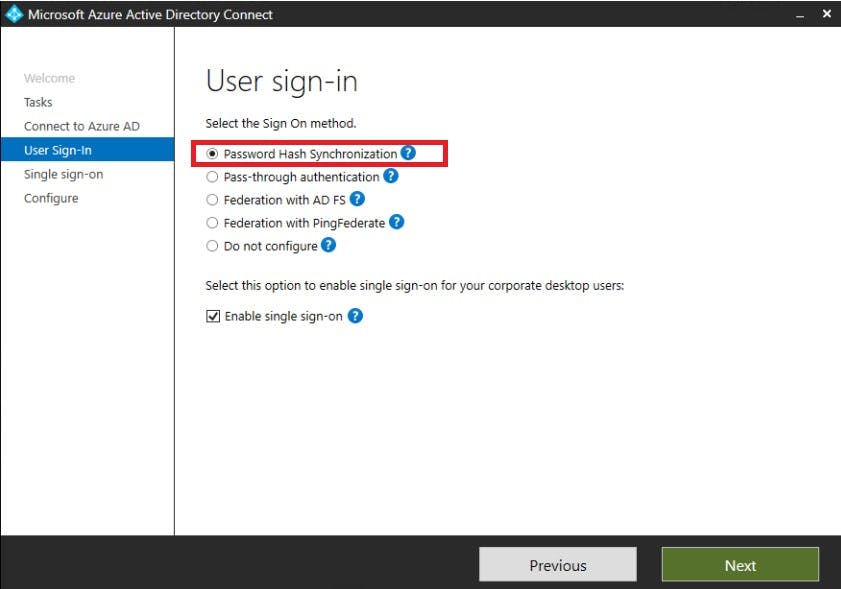
Enable Single sign-on by providing the Domain Administrator credentials for your on premise domain:
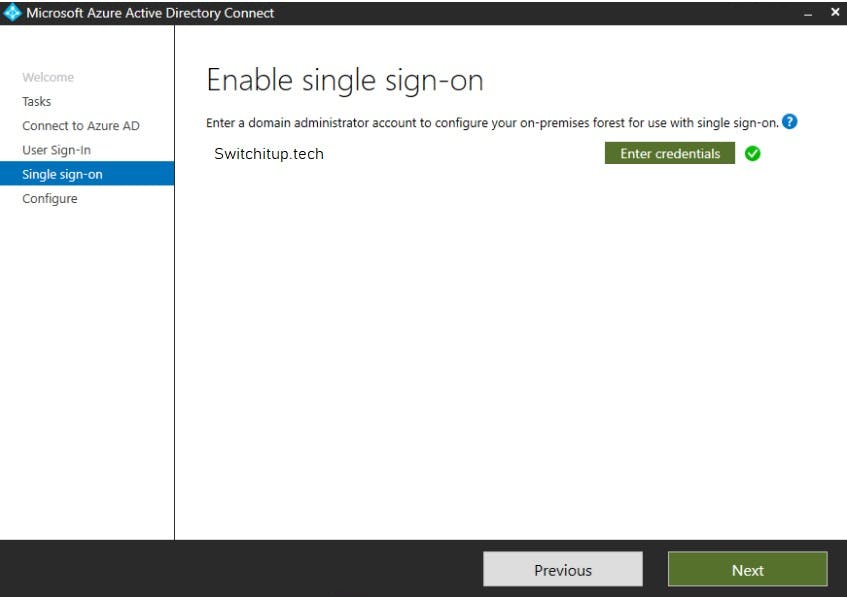
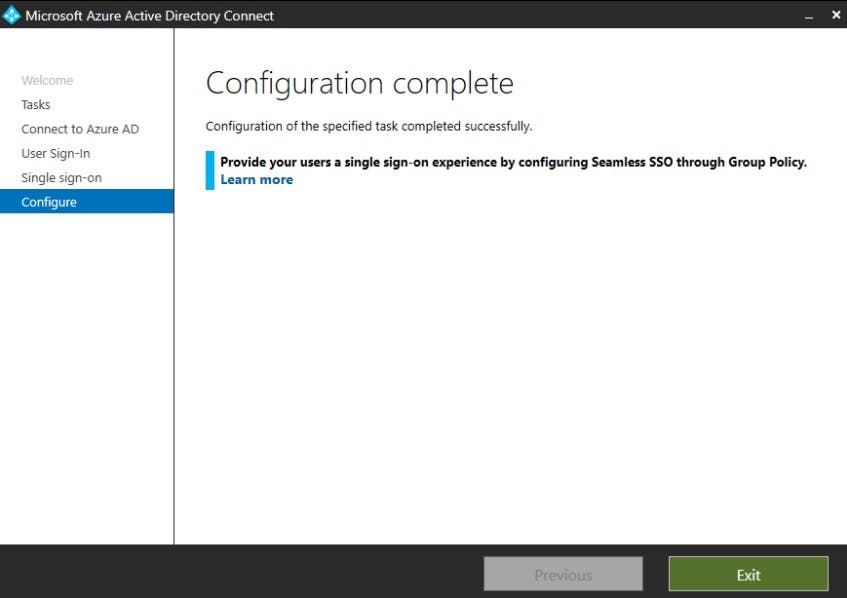
Remember syncing takes time based on the number of users! Microsoft estimates 20k users can take approximately an hour.
Create SSO GPO
Notice on the configuration complete screen it mentions setting up a GPO for SSO to work. Why do we need this?
"By default, the browser automatically calculates the correct zone, either Internet or Intranet, from a specific URL. For example, contoso maps to the Intranet zone, whereas intranet.contoso.com maps to the Internet zone (because the URL contains a period). Browsers will not send Kerberos tickets to a cloud endpoint, like the Azure AD URL, unless you explicitly add the URL to the browser's Intranet zone".
source: Microsoft.com
Create and edit a new GPO
Browse to User Configuration > Policies > Administrative Templates > Windows Components > Internet Explorer > Internet Control Panel > Security Page. Then select Site to Zone Assignment List.
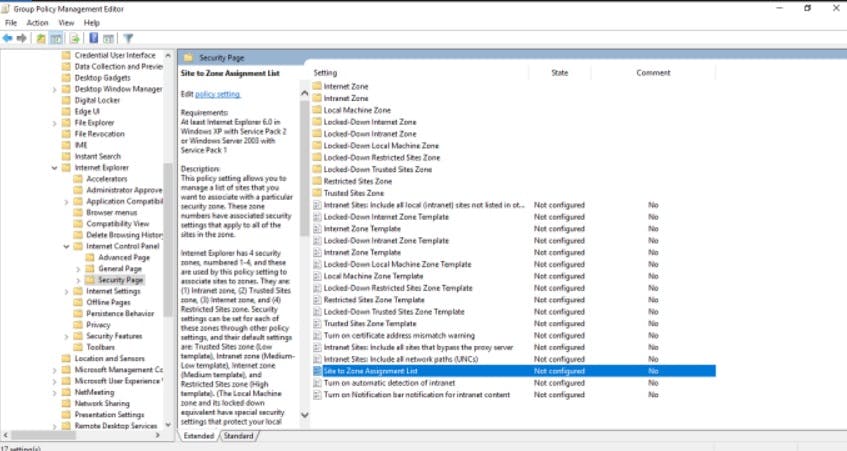
Edit the settings as follows:
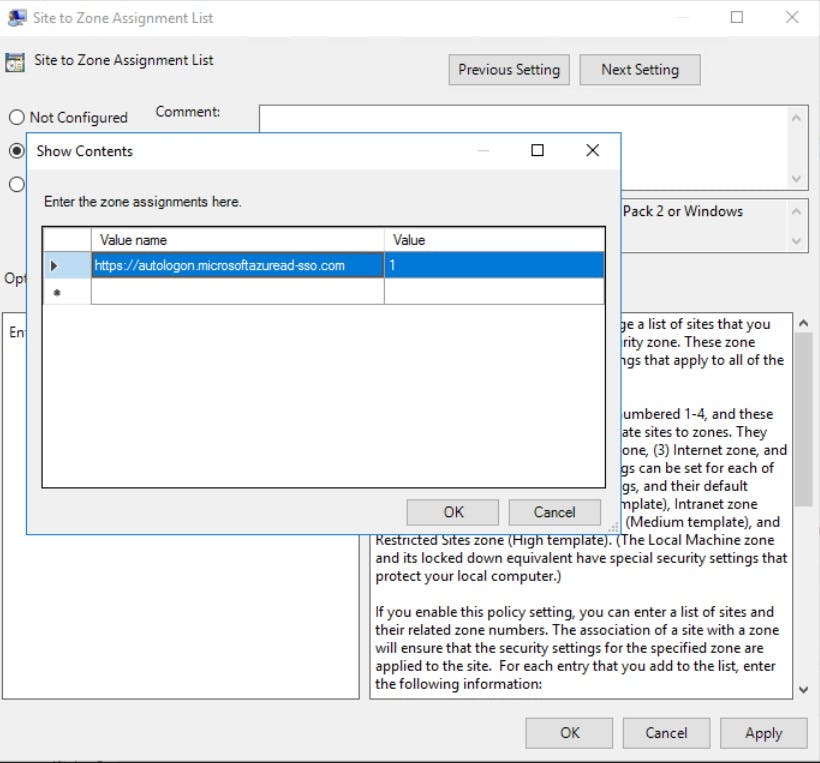
Finally
Browse to User Configuration > Policies > Administrative Templates > Windows Components > Internet Explorer > Internet Control Panel > Security Page > Intranet Zone. Then select Allow updates to status bar via script.
Enable the Policy.
If testing on a user machine remember to "gpupdate /force" to pull down your new policies.
All being well you should have Single Sign-on working for access to Microsoft cloud services and be running on Password Hash Sync.
You can also verify you sync method, Federation being disabled and single sign-on being used via the Azure portal:
Azure Active Directory > Azure AD Connect
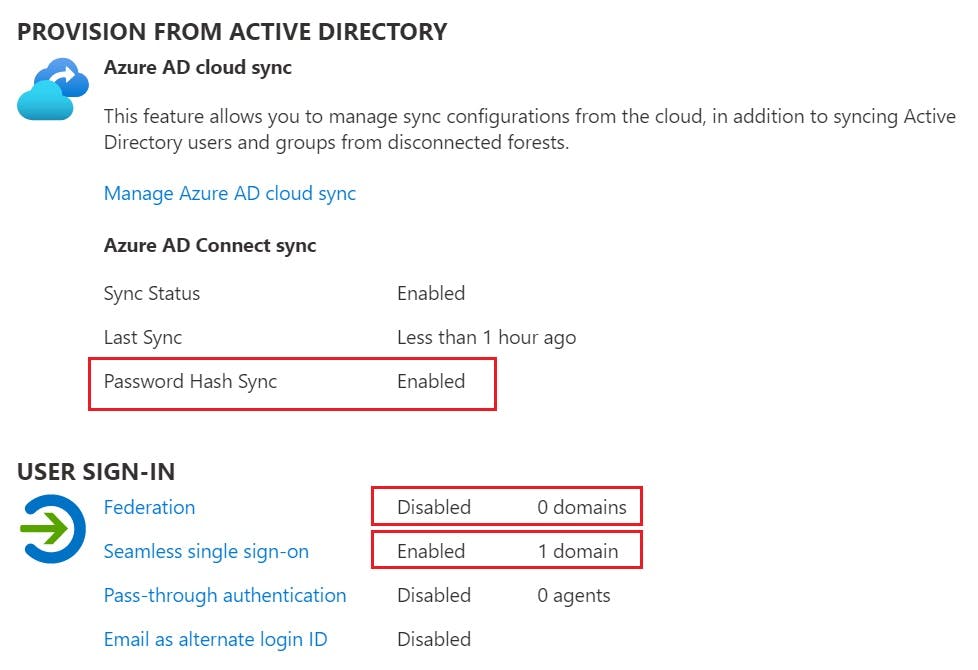
for more information on AD Connect and sync methods check Microsoft's documentation here:
docs.microsoft.com/en-us/azure/active-direc..